我是TNT-马嘉祺,我为时代少年团代言。

得分:
re/pwn
Heaps of Garbage
You’ve decided to look for treasure in various piles of garbage in a junkyard at
nc 3.23.56.243 9010. However, you must be careful: Some treasures contain lead, asbestos, or other poisonous materials, so make sure to avoid these treasures! Can you dive through all the garbage heaps and collect all the salvageable treasure while avoiding the toxic treasures?
一个二进制文件,反编译如下:
__int64 __fastcall main(int a1, char **a2, char **a3) |
堆布局:
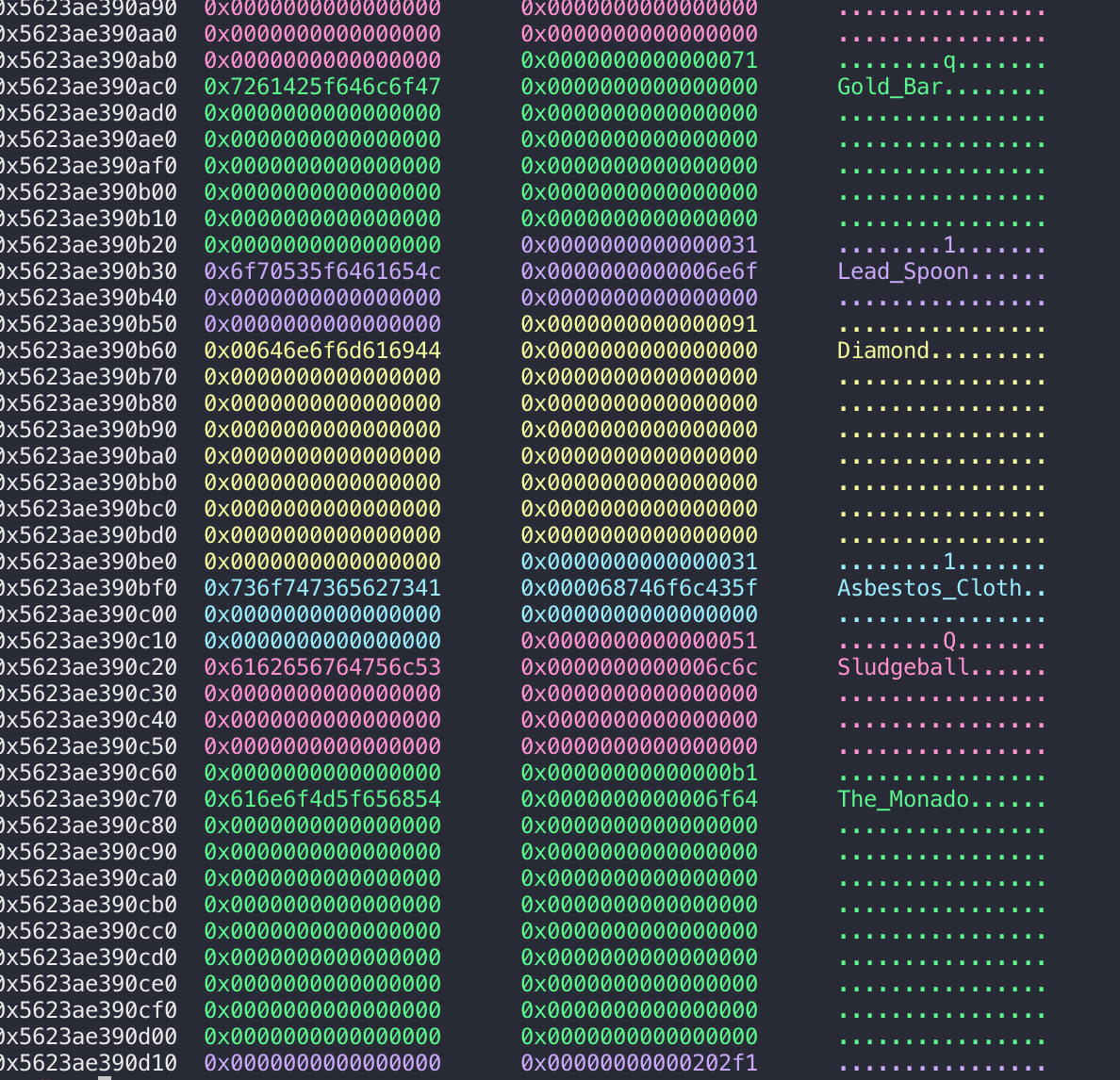
大致就是申请了一堆chunk,然后满足每个chunk有特定的字符串就行,exp如下:
from pwn import * |
flag:
Collatz-eral Damage
Can you find the correct flag? It’s hidden somewhere in this binary.
Flag format:
texsaw{<some string>}
主函数大致逻辑如下:输入flag,经过hailstone处理后,和一个密钥组对比。
int __fastcall __noreturn main(int argc, const char **argv, const char **envp) |
关于密钥组的处理shf函数如下:
void __fastcall shf(__int64 key, unsigned __int64 size_256) |
可以自己写一个C函数,然后拿初始的密钥数组进去运算,也可以直接gdb调内存,拷出来即可:
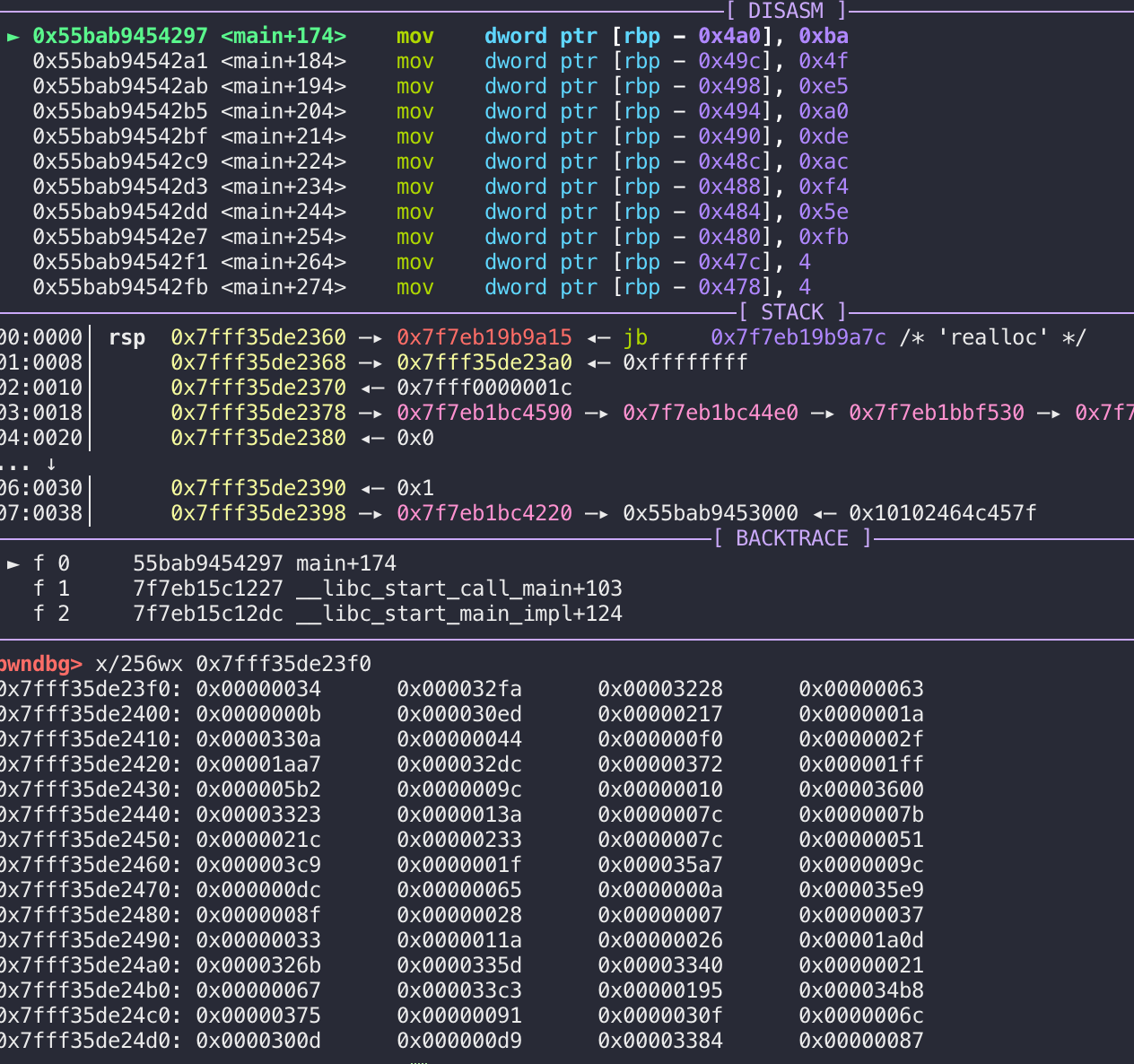
hailstone函数:
__int64 __fastcall hailstone(unsigned int val) |
解题脚本如下,直接爆破就行:
|
注意一下因为同一组ascii序列中可能有多个值符合要求,所以组合一下即可得到flag:
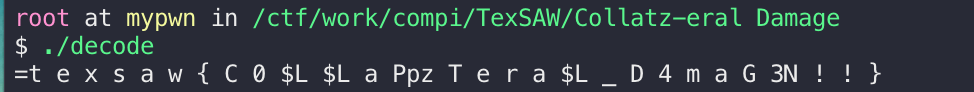
最终flag:texsaw{C0LLazTeraL_D4maG3!!}
Forensics
The Forked Cave
git泄露,但是不要用GitHack,GitHack对HEAD文件中的hash没有处理,导致object遗漏,推荐Git_Extract
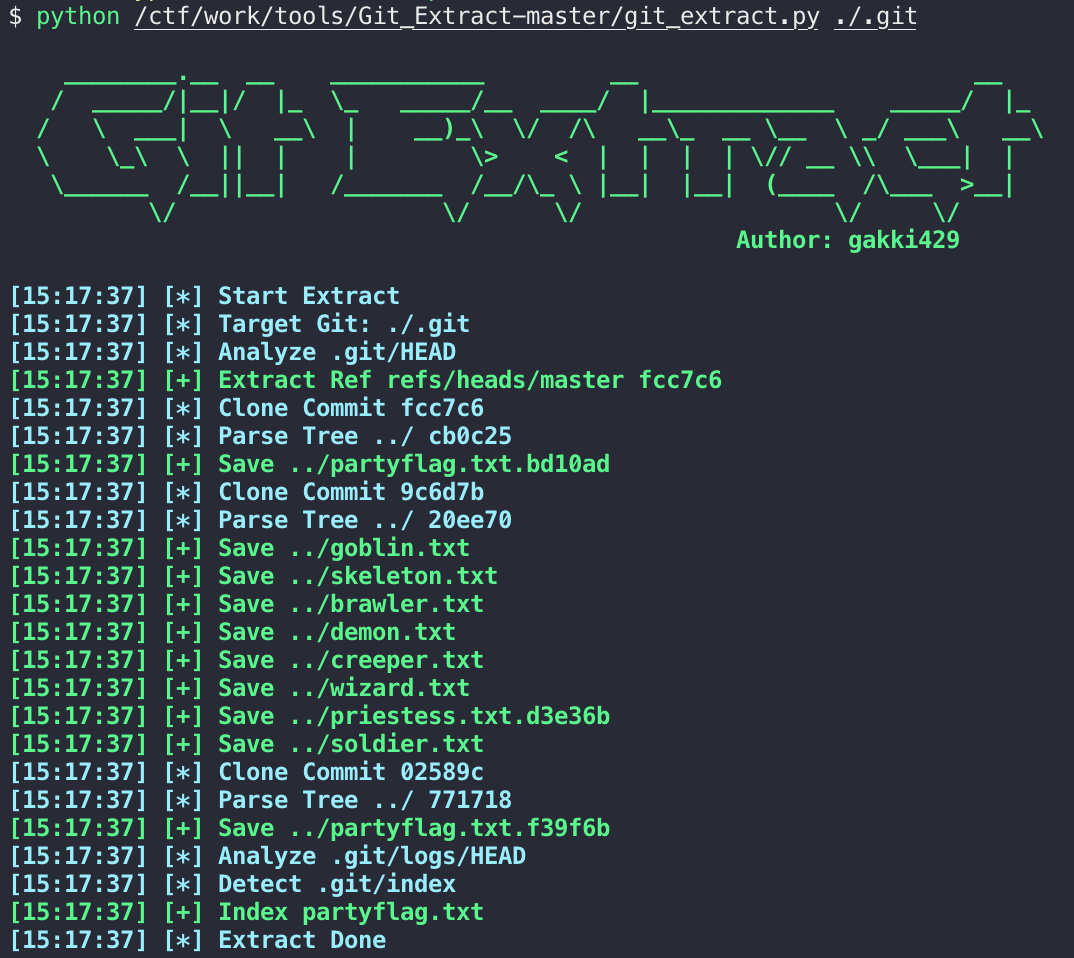
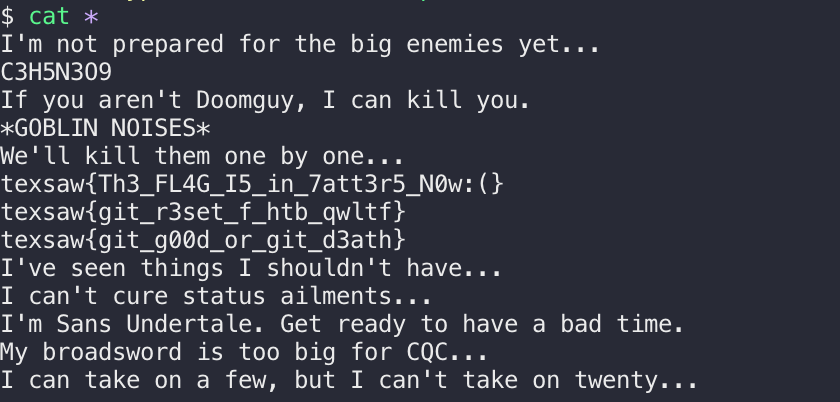
然后cat *:
MFMFT
I stole my boss’ flash drive. Rumor has it that he keeps the password to the payroll database fragmented across the filenames of the contents of his USB drive. I have a segment of the Master File Table here - can you help me figure out the password? I would like to give myself a 200% raise.
Oh, this might help:
[0, 10, 17, 18, 5, 6, 15, 13, 9, 16, 12, 5, 11, 1, 14, 5, 7, 6, 7, 3, 2, 2, 10, 8, 4, 7]Wrap what you find with
texsaw{}! If the password ispassword, entertexsaw{password}.
给了一个data文件,然后里面有若干FILE文件,先切成小份:
with open('../TheMFT', 'rb') as f: |
然后利用analyzeMFT提取信息,观察文件名后面就是密码,然后根据题目给的整数列表写个脚本提取:
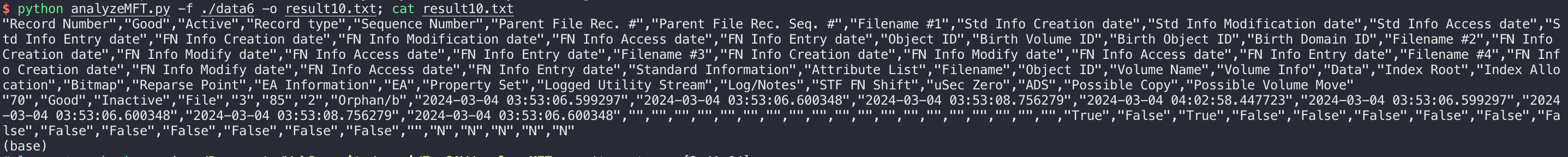
脚本如下:
In [7]: index = [0, 10, 17, 18, 5, 6, 15, 13, 9, 16, 12, 5, 11, 1, 14, 5, 7, 6, 7, 3, 2, 2, 10, 8, 4, 7] |
得到password:34sy_brEezY_MFT_7b7f224587
flag:texsaw{34sy_brEezY_MFT_7b7f224587}
MalWhere?
strings,发现一个ps脚本:
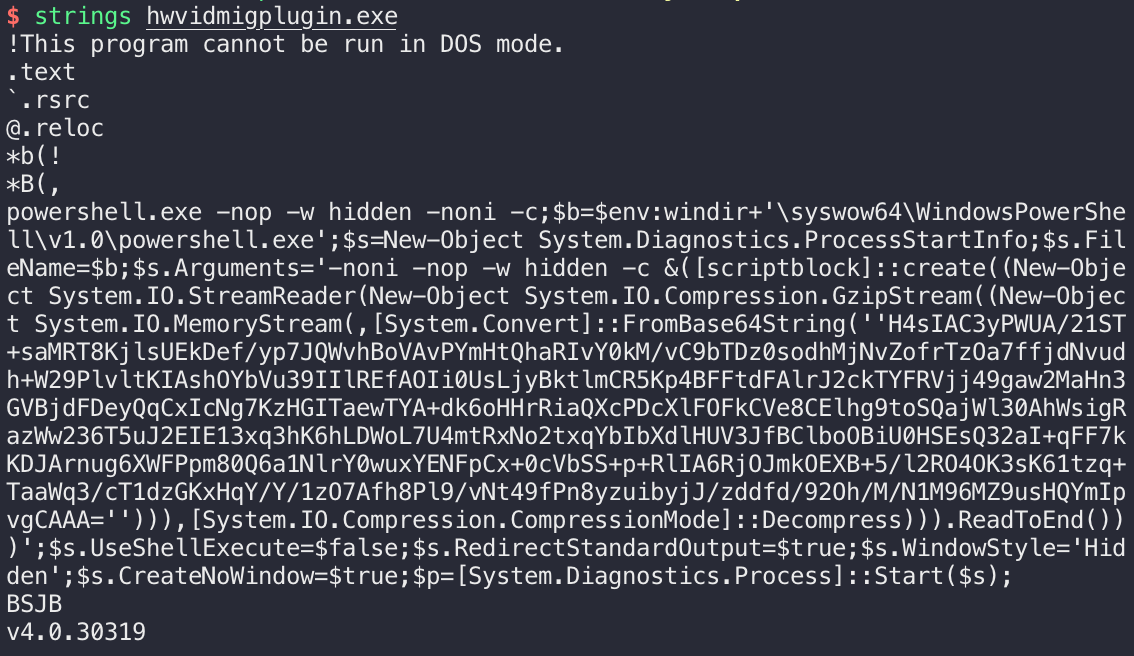
内容为:
powershell.exe -nop -w hidden -noni -c;$b=$env:windir+'\syswow64\WindowsPowerShell\v1.0\powershell.exe';$s=New-Object System.Diagnostics.ProcessStartInfo;$s.FileName=$b;$s.Arguments='-noni -nop -w hidden -c &([scriptblock]::create((New-Object System.IO.StreamReader(New-Object System.IO.Compression.GzipStream((New-Object System.IO.MemoryStream(,[System.Convert]::FromBase64String(''H4sIAC3yPWUA/21ST+saMRT8KjlsUEkDef/yp7JQWvhBoVAvPYmHtQhaRIvY0kM/vC9bTDz0sodhMjNvZofrTzOa7ffjdNvudh+W29PlvltKIAshOYbVu39IIlREfAOIi0UsLjyBktlmCR5Kp4BFFtdFAlrJ2ckTYFRVjj49gaw2MaHn3GVBjdFDeyQqCxIcNg7KzHGITaewTYA+dk6oHHrRiaQXcPDcXlFOFkCVe8CElhg9toSQajWl30AhWsigRazWw236T5uJ2EIE13xq3hK6hLDWoL7U4mtRxNo2txqYbIbXdlHUV3JfBClboOBiU0HSEsQ32aI+qFF7kKDJArnug6XWFPpm80Q6a1NlrY0wuxYENFpCx+0cVbSS+p+RlIA6RjOJmkOEXB+5/l2RO4OK3sK61tzq+TaaWq3/cT1dzGKxHqY/Y/1zO7Afh8Pl9/vNt49fPn8yzuibyjJ/zddfd/92Oh/M/N1M96MZ9usHQYmIpvgCAAA=''))),[System.IO.Compression.CompressionMode]::Decompress))).ReadToEnd()))';$s.UseShellExecute=$false;$s.RedirectStandardOutput=$true;$s.WindowStyle='Hidden';$s.CreateNoWindow=$true;$p=[System.Diagnostics.Process]::Start($s); |
大概是创建一个新的ps脚本并执行,新脚本被压缩然后base64编码了,首先还原脚本:
In [1]: import base64 |
得到:
$op = [char[]]@([int](503%107+41),[int](732%105-1),[int](349%229+0),[int](984%850-19),[int](341%245+1),[int](702%588+5),[int](422%146-7),[int](832%672-48),[int](981%102-15),[int](541%150+28),[int](251%102+22),[int](894%712-68),[int](201%103-15),[int](639%240-42),[int](387%110+25),[int](472%342-27),[int](173%109+5),[int](306%181+0));$ra = [char[]]@([int](734%161+2),[int](251%90+5),[int](542%110+3),[int](802%345-14),[int](943%810-19),[int](256%158-1),[int](238%130+6),[int](823%715-3),[int](942%281+2),[int](204%103+14),[int](291%100+1),[int](422%150-6),[int](439%328+9),[int](143%72+45),[int](103%57+0),[int](743%212-4),[int](642%553+8),[int](932%164-4),[int](398%143-10));$lr= $ra -join '';$ax=$op -join '';$b=$env:PUBLIC + $lr;$ax | Out-File -FilePath $b; |
这个就比较明显了,一个字符数组存了一堆ascii,可以用python筛选出所有的算式,运算后得到flag:
import re |
Cryptography
Ironcrypt
Commander, we managed to gain access to the Ironblood’s encryption servers, but we only know the key. If we get the IV, we will be able to decrypt all of their messages, locate their submarines, and win the war!
nc 3.23.56.243 9013
源码如下:
from binascii import hexlify, unhexlify |
给定了一个密码系统,可以提供明文输入,获取密码输出,并且已知key,题目让求iv:
$ nc 3.23.56.243 9013 |
根据OFB解密流程,我们只需要将密文和明文异或,就可以得到key和iv的密码块了,只需要提供key就可以解出iv:
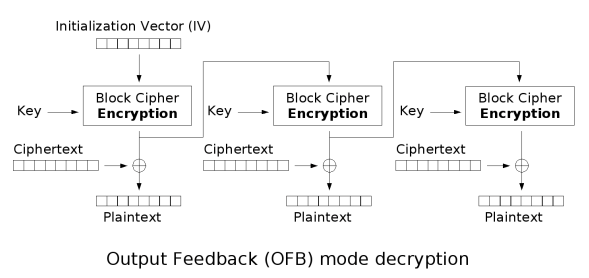
解密脚本:
from binascii import hexlify, unhexlify |
得到flag后半部分:
Web
Login Attempt
万能密码秒了
Out of Bounds
I really HATE game developers. So much so that when I receive a new game, my priority is not to beat the game, but to find out how to go to places I’m not supposed to. I made a cool guide on several video games with out-of-bounds glitches which you can find at
3.23.56.243:9004. Do you have any additions to recommend??
题目提示测试边界:
路由界面输入-1就过了

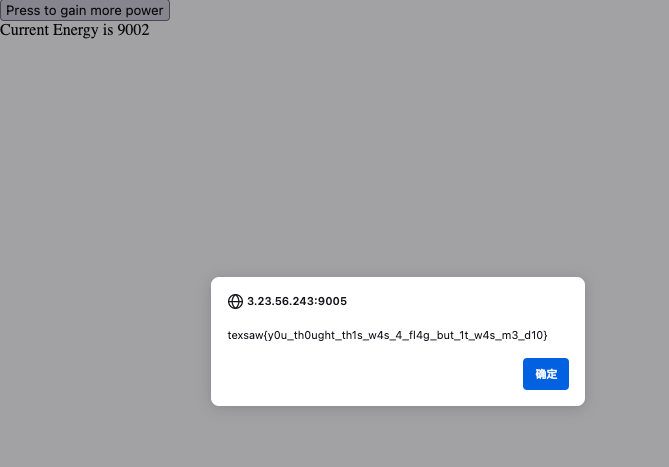
Crazy Cookie
I can’t seem to login to the account to
3.23.56.243:9002. Can you help me get access?
抓包改cookie秒了
GET / |
Extreme Security
We are at
3.23.56.243:9003. We are so secure that we only allow requests from our own origin to access secret data.
观察响应报文:
200 OK |
有个CORS检查,Access-Control-Allow-Origin: https://texsaw2024.com
加个Origin,发送报文:
GET / |
拿到flag:
200 OK |
Over 9000
Help Goku get over 9000 energy to defeat his enemy Vegeta and save the world.
观察js文件:
|
有个currentEnergy变量控制点击次数
直接在控制台输入:currentEnergy=9001
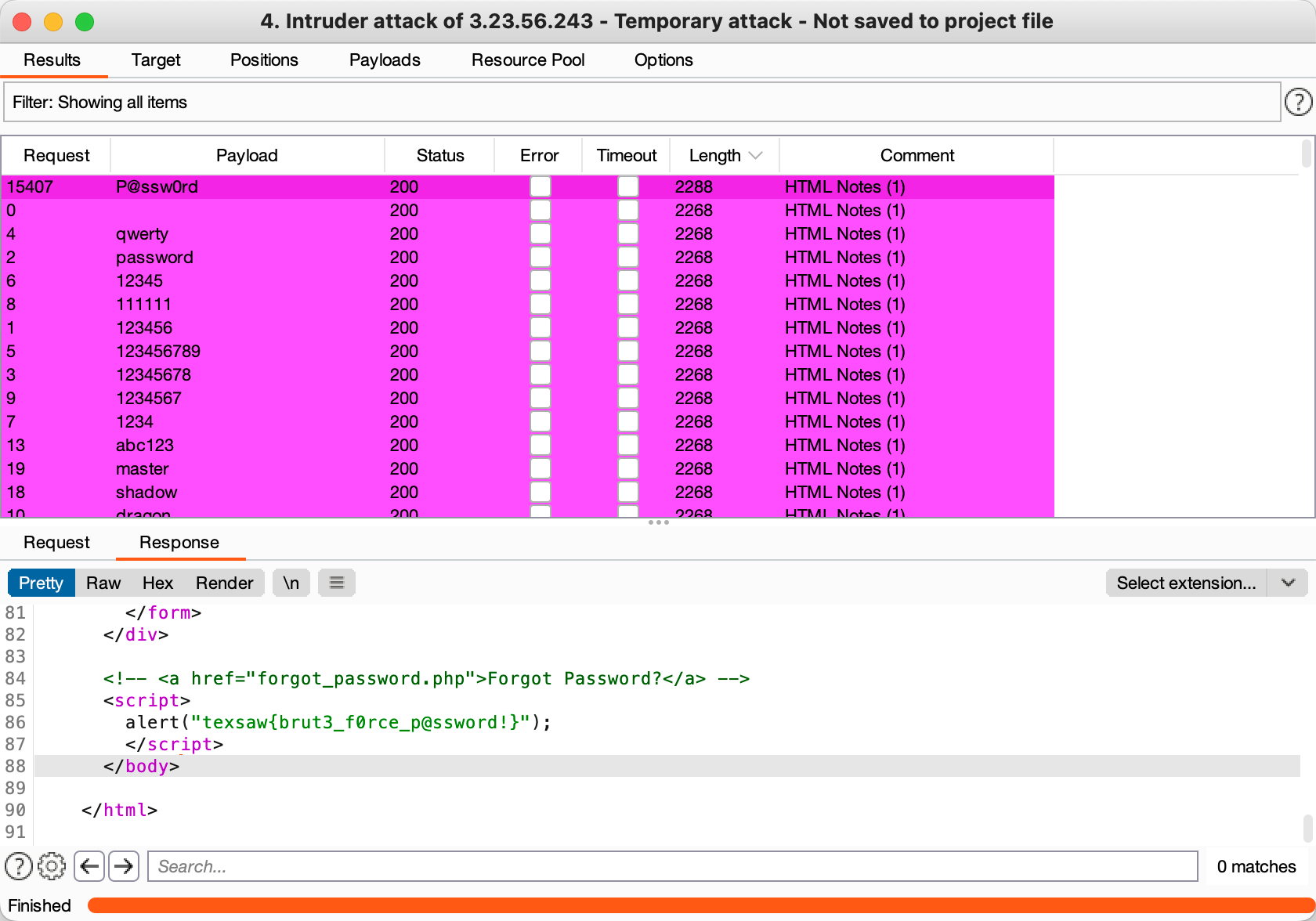
Insecure Social Media Login
Your friend John has forgotten his password and wants to enlist the help of his tech savy friend. This is where you come in.
You’re going to have to find a way to remember John’s password. The site is at
3.23.56.243:9007This social media site looks insecure, like it probably doesn’t limit the number of guesses users can make…
弱口令,上强度,大字典直接爆破,没啥意思
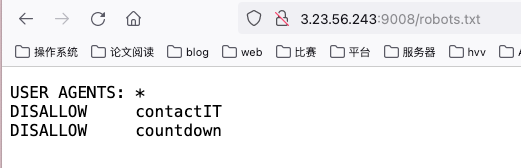
Ask, and It Shall Be Given to You
The flag is at
3.23.56.243:9008. Unfortunately it seems like the site is down right now :( . Maybe you can ask someone for help? Don’t blow up their inbox though :) and make sure you clearly tell them what you want.
访问robots.txt有如下内容:
访问countdown路由:http://3.23.56.243:9008/countdown
尼玛,大半夜吓👴🏻一跳

访问contactIT路由:
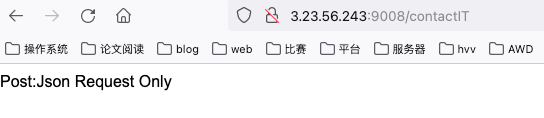
提示post json数据:
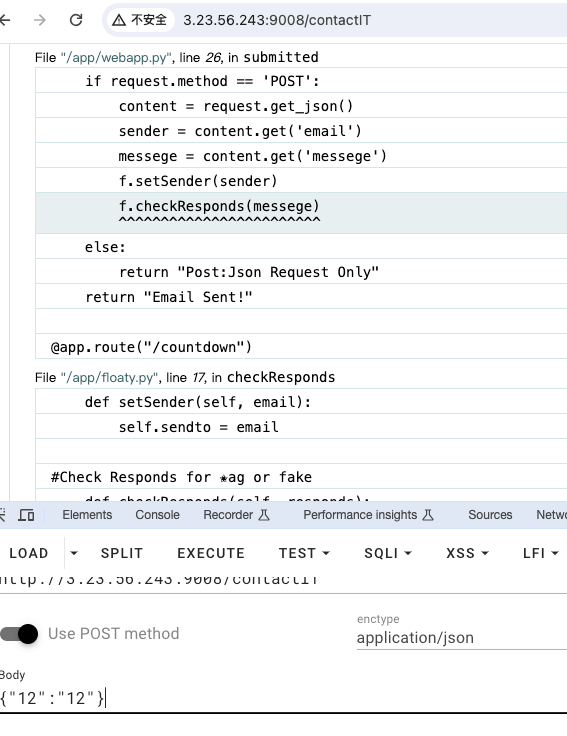
随便发发,通过debug信息大致可以看到要发emal和message(出题人老丈育了)两种消息,部分debug信息如下:
<!doctype html> |
反正大致就是messege字段填flag,然后找个邮箱来接flag:
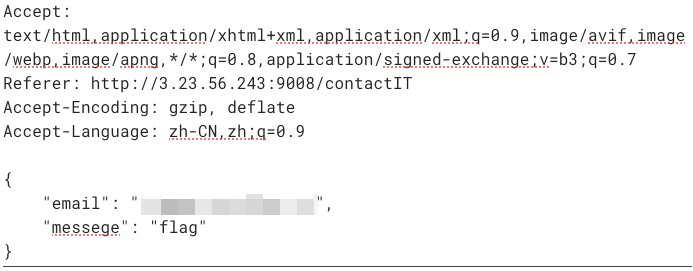
彳亍:

